Prescreening Ingredients for a Food Fraud Vulnerability Assessment
Prioritizing ingredients for food fraud vulnerability assessments can be done in four simple steps, using the Food Chemicals Codex prescreening guidance.
Article Content
Food fraud is a significant threat, affecting not only the integrity of the food supply chain but public health as well. For example, in 1981, adulterated cooking oil resulted in more than 20,000 illnesses and up to 600 deaths in Spain (Kilbourne et al. 1991); likewise, 294,000 illnesses and at least six deaths occurred in infants and children in China in 2008 as a result of melamine in milk products (Gossner et al. 2009). More recently, the Canadian Food Inspection Agency found that 21% of honey samples collected in 2018 were adulterated with added sugar (CFIA 2019), while in Europe, authorities seized more than 16,000 metric tons of fraudulent food items and arrested 672 individuals during a five-month operation that started in December 2018 (Europol 2019).
Although the full extent of food fraud in the supply chain will never be known, in part because successful fraudsters are seldom caught, it has been found that up to 50% of samples of particularly vulnerable commodities have been adulterated (Wielogorska et al. 2018). The problem is compounded by increasing opportunities for misrepresentation due to the number of food products that carry claims such as organic, sustainable, fair trade, or local. Sudden changes in supply chains also create opportunities for fraud and adulteration.
Widespread recognition of the consequences of food fraud, such as followed the 2008 melamine and the 2013 horse meat incidents, have alerted the food industry to the need to identify and limit fraud. One manifestation of this awareness was the publication of a position paper by the Global Food Safety Initiative (GFSI) in 2014 on mitigating the risk from food fraud. The paper was followed by GFSI benchmarking requirements to conduct a fraud vulnerability assessment and develop a mitigation plan, which started with version 7.
To help organizations develop scientifically sound vulnerability assessments and effective mitigation plans, the United States Pharmacopeia Food Adulteration Expert Panel (EP) developed a Food Fraud Mitigation Guidance (FFMG) that was published in the Third Supplement of the 9th Edition of the Food Chemicals Codex (2015). The guidance recognized that, because food fraud is an intentional act, effective fraud vulnerability assessments must use tools specifically designed to address the issue rather than those designed to assess food safety risks.
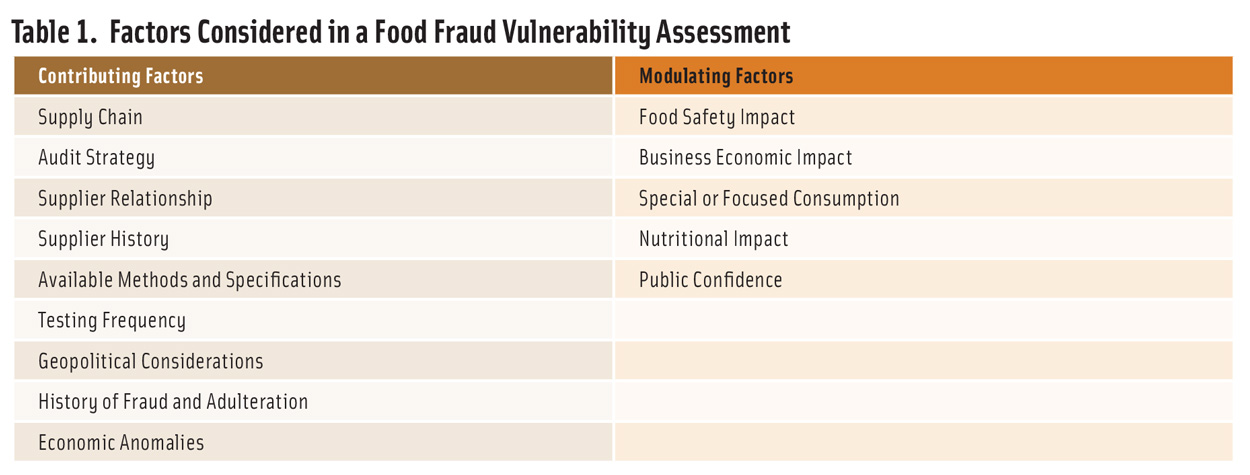
The guidance identified nine factors that contribute to vulnerability and five factors that modulate impact (Table 1). To conduct a vulnerability assessment, each factor is rated on a five-step scale, and two sets of factors are combined to create a final vulnerability estimate. The process is intended to be carried out independently for each ingredient (or family of related ingredients) used by a facility. In addition to the vulnerability evaluation, the process provides insight on where to implement changes or controls that will have the greatest impact.
After the FFMG was published, USP worked with several companies to carry out vulnerability assessments using the FFMG. These companies included both large and medium-sized manufacturers in different industry segments. The results showed that the process described in the FFMG was highly effective, although facilities working with many ingredients could find it operationally challenging to implement a complete ingredient-by-ingredient fraud evaluation. It became clear that the best way to address the difficulty was to conduct a prescreen to identify ingredients at greatest risk of fraud or adulteration and focus initial evaluation and mitigation efforts on those ingredients. Limiting the full-scale vulnerability assessment to a more tractable subset of ingredients makes it possible to significantly reduce risk and create a realistic workflow for continuous improvement. Therefore, the EP added guidance on how to conduct an ingredient prescreen to the FFMG. The revised FFMG has been published in the First Supplement of the 12 Edition of the FCC (2020).
It is important to recognize that the prescreen is a process for initial prioritization and not a substitute for the FFMG vulnerability assessment (see definitions in sidebar). It is not intended to eliminate ingredients from further consideration but to focus efforts where they will be most useful. Because all ingredients have some degree of vulnerability, and the factors that affect vulnerability change over time, the prescreen should be repeated regularly. In addition, reassessment of prescreens and of full vulnerability assessments should be triggered by events such as new reports of adulteration, price fluctuations, supply chain disruptions, or changes in suppliers.
Is a Prescreen Needed?
Whether a company or facility needs to use a prescreen depends on factors such as the number of ingredients handled, the complexity of the supply chains, the number and products produced, and the results of previous assessments. In many cases, the decision to use a prescreen will depend on the intended consumer, available resources, corporate enterprise risk management tolerance, regulatory requirements, and customer commitments such as certification to audit schemes. A food fraud prescreen, like a food safety hazard analysis, should not be considered a one-time activity but should be updated regularly, preferably at least annually.
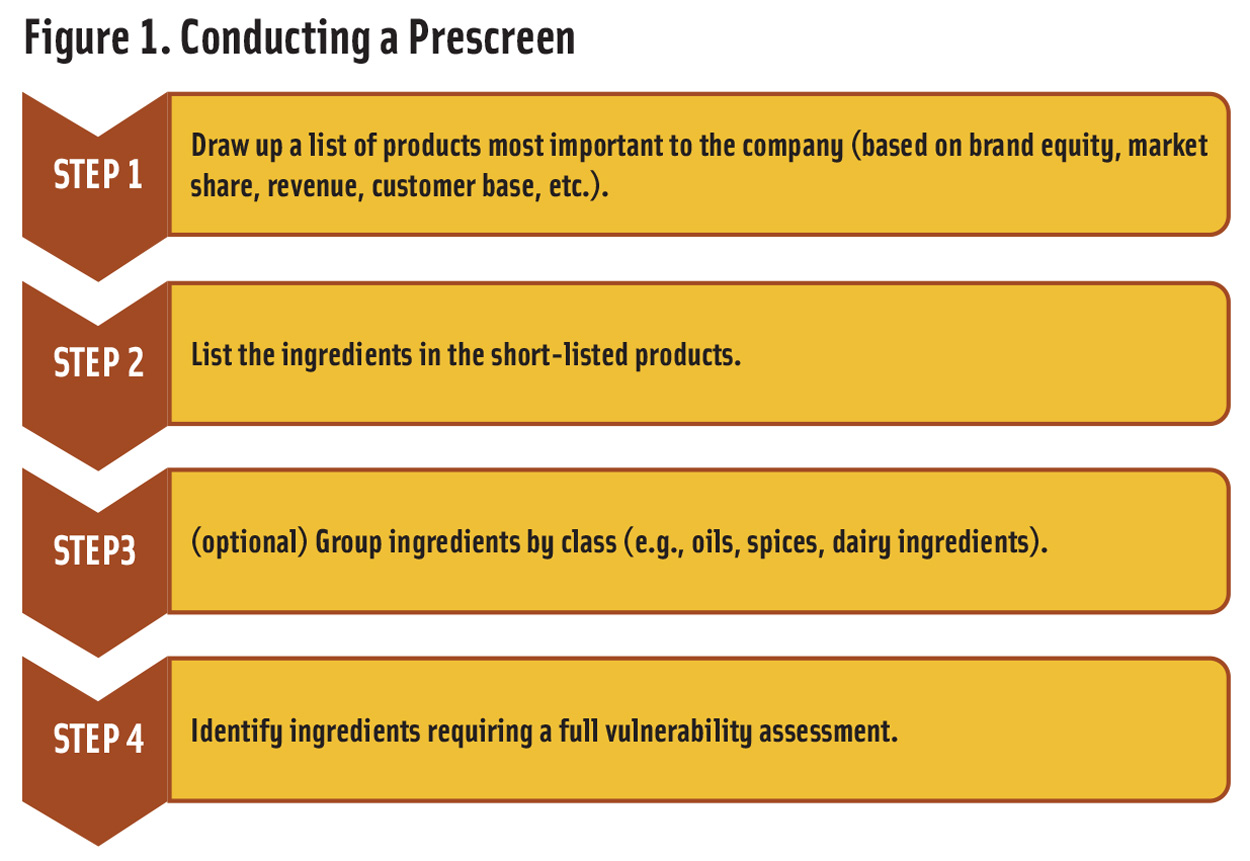
The prescreen is carried out in four steps (Figure 1). The first three involve data gathering while the last is an evaluation. The first step is to identify products that are most important to the company. The factors that should be considered include brand equity, market share, contribution to revenue, cost to produce, and the target consumer base. This step is not necessary for companies with a small number of final products or with a portfolio of very similar products. For example, a company that makes a wide variety of grocery items will need the evaluation while a company that makes a limited range of energy bars with only a few ingredient differences will not.
Step 2 is to compile a complete list of the ingredients used in the products identified in Step 1. In addition to ingredient declarations, the list should include flavors, processing aids, indirect additives, and sub-ingredients, even if they are not required to be declared on the package. Other important information, such as whether an ingredient has additional value because it claims to be organic, gluten-free, or sourced from a specific location, should be noted. To simplify further, in an optional Step 3, similar ingredients, such as all plant oils or all dairy products, can be grouped together.
Step 4 is to evaluate each ingredient or group of ingredients identified in Steps 2 and 3 as described below. Each of the high-priority ingredients identified in Step 4 should then be evaluated using a vulnerability assessment.
Prioritizing Ingredients
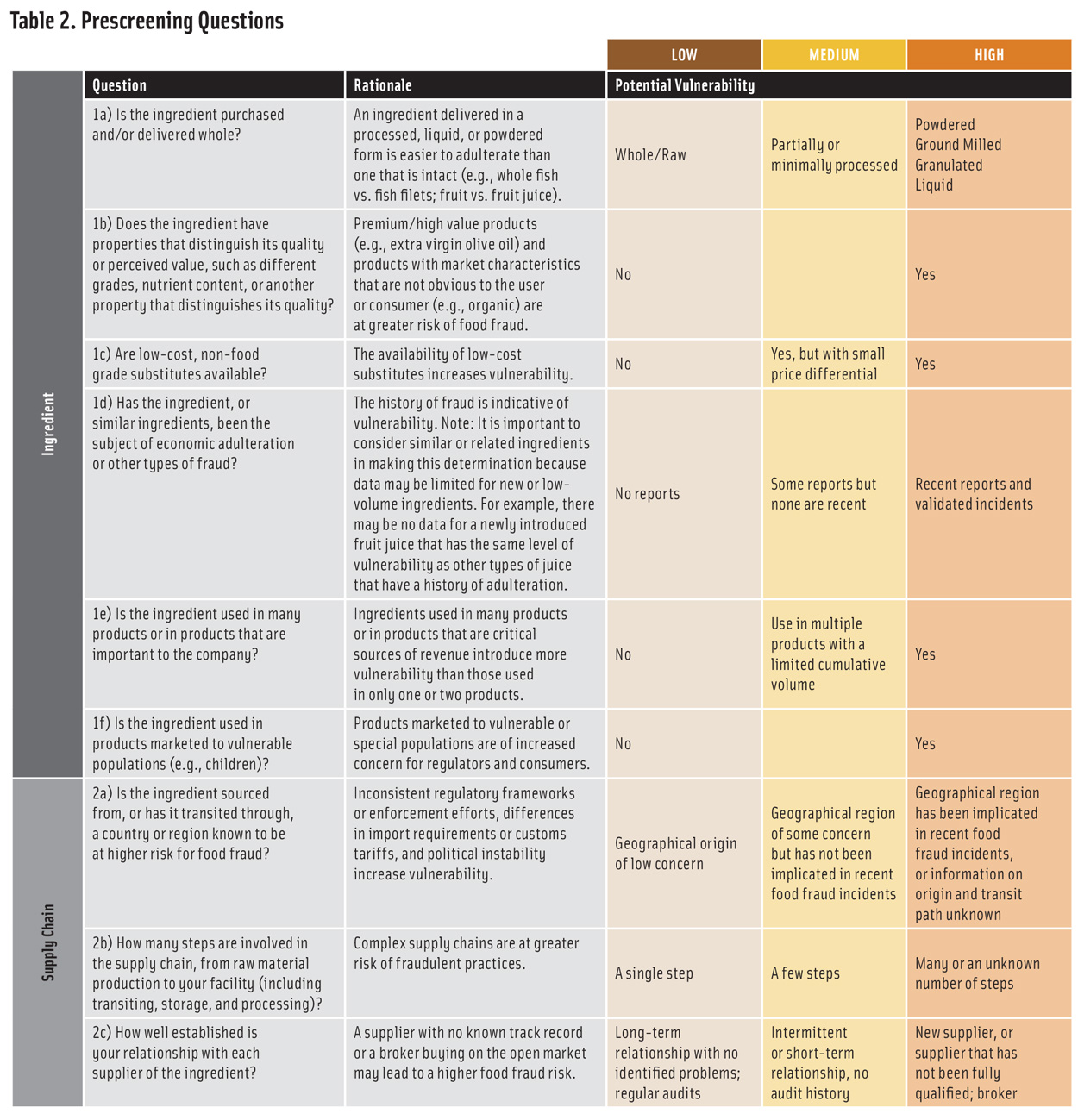
The ingredient evaluation is carried out by answering a set of questions related to the ingredient itself and its supply chain. Although there are many ways to structure the evaluation, the questions in Table 2 address the most critical factors. The answers to the questions provide a qualitative (low, medium, or high) evaluation of potential vulnerability. In situations where the answer is unknown, high vulnerability should be assumed. This ensures that the prescreen is maximally protective and recognizes that, if the results lead to a vulnerability assessment, the additional considerations involved will provide a more robust evaluation. The table can be modified to meet company needs, but the basis for any modifications should be documented.
To facilitate ingredient ranking, the evaluation can be made semi-quantitative by assigning a score to each vulnerability level and combining the scores from each line in the table to create an overall ingredient vulnerability score. There are several ways to assign scores. Using a scale that places more emphasis on high vulnerability (such as 1-5-7 for low-medium-high) is more protective and more likely to clearly differentiate between ingredients than one that does not (such as 1-2-3 for low-medium-high). The questions can be weighted differently based on company experience and concerns. For example, for some ingredients, question 1a about whether an ingredient is obtained whole or processed may be considered as carrying more weight than question 1b about distinguishing properties. The basis for choosing a scoring and weighting scheme should be clearly documented.
It is important to recognize that the use of a numeric system is only to facilitate ranking among ingredients that have been assessed in a consistent manner. The actual values have no absolute meaning and cannot be used to compare vulnerabilities between different prescreens.
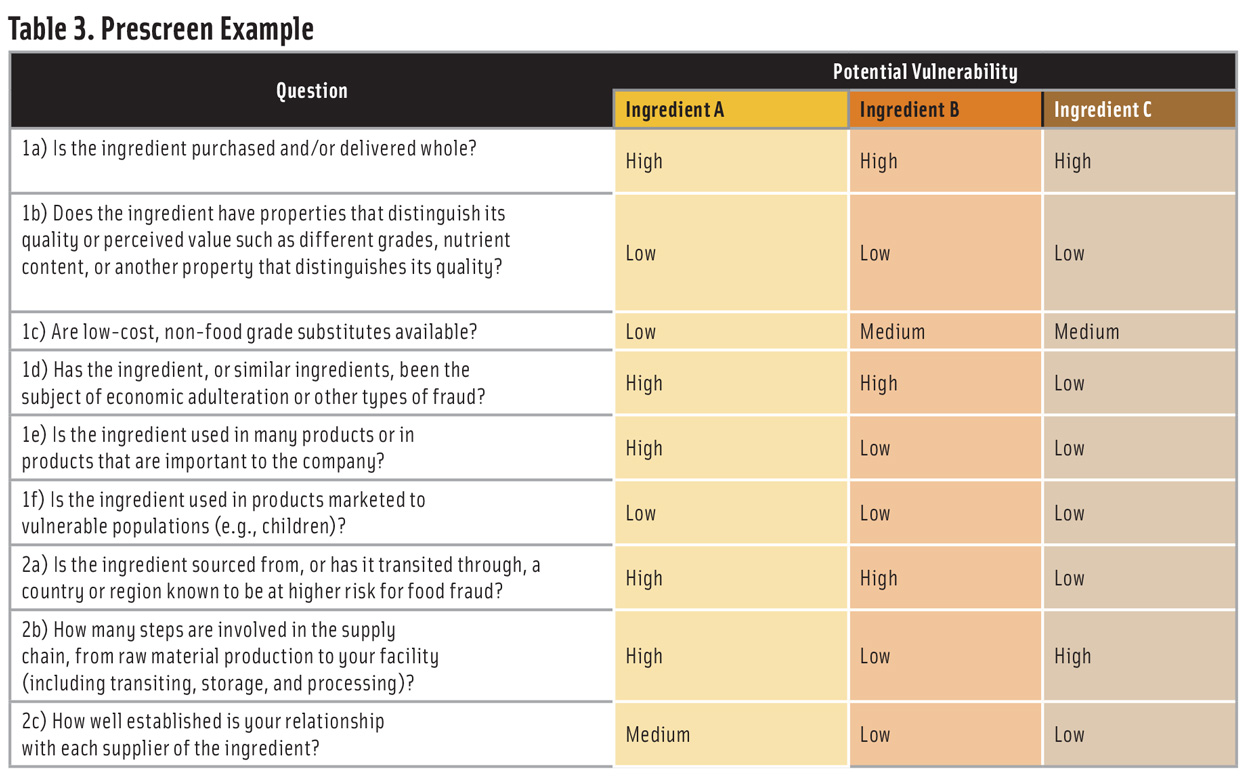
Table 3 shows an example of a prescreen for three ingredients (A, B, and C). Using a 1-3-7 scoring system for low-medium-high potential vulnerability—and weighting all the questions equally—would result in a ranking of Ingredient A >> Ingredient B > Ingredient C. Based on this ranking, a company would identify Ingredient A as high priority for a vulnerability assessment and Ingredients B and C as lower priority.
A company that handles many ingredients may find that a prescreen with three vulnerability levels will result in clusters of ingredients with the same score. In this case, all the ingredients in the cluster with the highest vulnerability should be considered for a vulnerability assessment.
Next Steps
The prescreen process is intended to be a rapid way to differentiate among many ingredients to determine which are of highest priority for the food fraud vulnerability assessment described in the FFMG. The prescreen and vulnerability assessment together provide an easily documented, thorough, and structured approach to conducting vulnerability assessments, either for internal business uses or to satisfy requirements of a GFSI recognized audit scheme. The structures used make it possible to identify whether improved mitigation strategies are needed, and, if so, where the most impactful changes can be made.
Feedback from users of the prescreen and vulnerability assessment will be used by FCC experts to improve these tools as the fraud landscape evolves.
REFERENCES
CFIA. 2019. Enhanced honey authenticity surveillance (2018 to 2019). Rept. Canadian Food Inspection Agency, Ottawa, Ontario, Canada. https://www.inspection.gc.ca/about-cfia/science-and-research/our-research-and-publications/report/eng/1557531883418/1557531883647.
Europol. 2019. “Over €100 million worth of fake food and drinks seized in latest Europol-Interpol operation.” Press release, June 19. Europol, The Hague, The Netherlands. https://www.europol.europa.eu/newsroom/news/over-%E2%82%AC100-million-worth-of-fake-food-and-drinks-seized-in-latest-europol-interpol-operation.
Gossner, C. M., J. Schlundt, P. Ben Embarek, et al. 2009. “The Melamine Incident: Implications for International Food and Feed Safety.” Environ Health Persp 117: 1803–1808.
Kilbourne, E.M., M. Posada de la Paz, I. Borda, et al. 1991. “Toxic oil syndrome: a current clinical and epidemiologic summary, including comparisons with the eosinophilia-myalgia syndrome.” J Amer Coll Cardiol 18: 711-717.
Wielogorska, E., O. Chevallier, C. Black, et al. 2018. “Development of a comprehensive analytical platform for the detection and quantitation of food fraud using a biomarker approach. The oregano adulteration case study.” Food Chem 239: 32–39.