Beyond Ransomware: Securing the Digital Food Chain
As a new breed of cyberbiosecurity threats emerges, it’s time for the food and agriculture system to address gaps in education, investment, and transparency.
Article Content
In May 2021, the world’s largest meat processor, JBS Foods, paid $11 million in Bitcoin to a ransomware gang known as REvil, following a cyberattack that forced JBS to halt operation in 13 of its U.S. beef processing plants. When Andre Nogueira, CEO of JBS USA, confirmed the ransom payment, he said JBS did so to mitigate damage to supply chain partners, including restaurants, grocery stores, distributors, and ranchers.
The JBS incident is the latest in a spate of ransomware attacks on major food and beverage companies over the past year, including Molson Coors, Campari Group, and Brown-Forman. Further, since 2015, several U.S. restaurant and fast-food chains suffered malware attacks resulting in expensive data breach lawsuits, including Caribou Coffee, Applebee’s, Panera Bread, Chipotle, Sonic Drive-In, Pizza Hut, KFC, Wendy’s, and Dunkin’.
A 2017 cyberattack against Mondelēz International resulted in significant operational disruption to its production, distribution, and sales and financial losses. The Mondelēz incident is noteworthy because it highlighted the limits of cyber insurance coverage and the role of exclusions, which remains an ongoing debate (Satariano and Perlroth 2019). Additionally, small to medium-size businesses, which often do not have the in-house technical support or security of large corporations, serve as farm-to-table supply chain partners throughout the system; attacks on these companies may be equally disruptive with significant operational and financial losses.
A Sweeping, Multidimensional Challenge
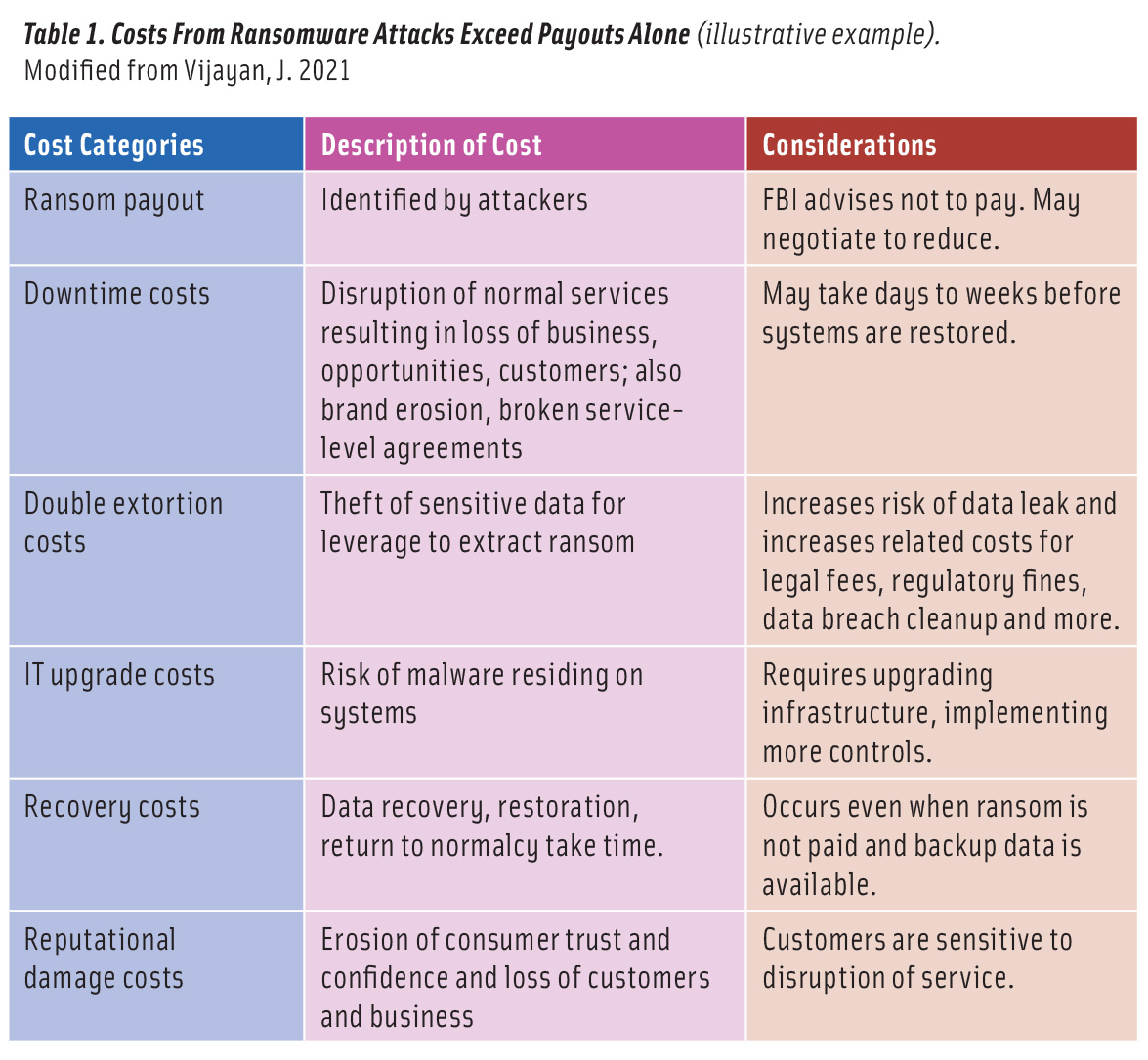
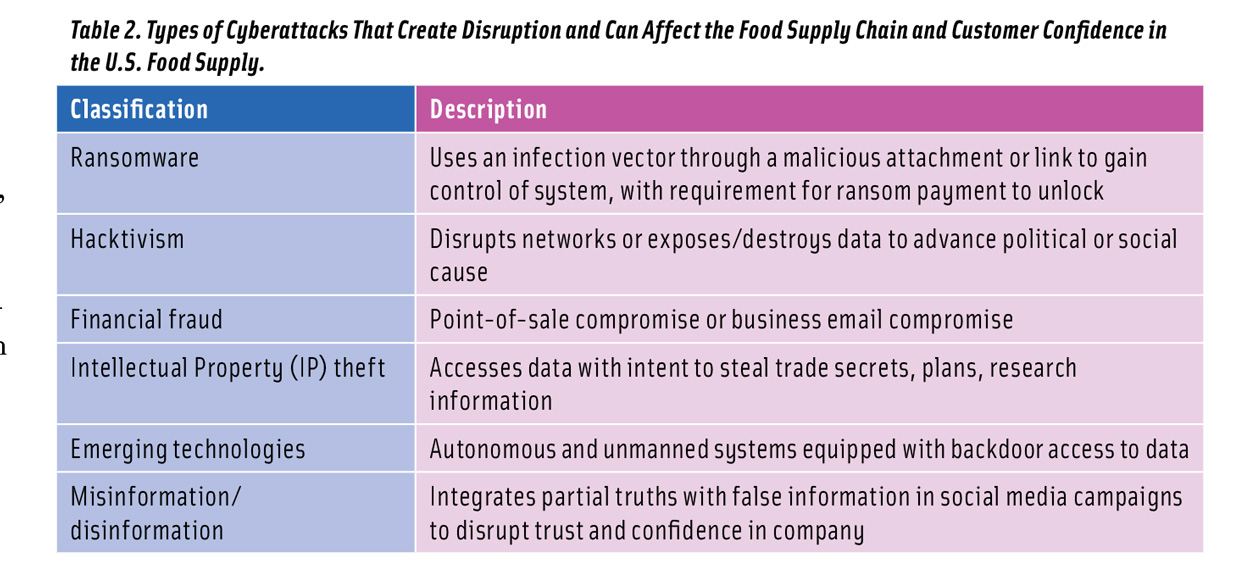
Costs associated with ransomware can rapidly escalate (Table 1), exceeding the ransom itself. Cyber threat tactics and techniques are constantly evolving, and while the prevalence of cyberattacks is increasing within the foodservice and food processing sectors, the landscape of cyber threat and vulnerability is not one-dimensional, nor are the characteristics of cyber threat actors (Table 2). Cyber threat actors can comprise malign states, criminal or transnational criminal syndicates, lone wolf mercenaries, hacktivists, insider threat actors (including disgruntled employees), dissatisfied customers, homegrown violent criminals or extremist groups, foreign terrorist organizations, and industrial competitors.
The increasing number of cyberattacks on large food and beverage companies is part of a growing trend by cyber threat actors to target critical infrastructure sectors, including food and agriculture, which increasingly depend on information technology (IT), operational technology (OT), and convergent IT-OT or Internet of Things (IoT) processes and applications to increase efficiencies, optimize processes, and enhance knowledge discovery and innovation. The high value of the diverse integrated data sets used in food and agriculture research, development, production, and distribution has created a rich environment for cybercriminal interfere with uniquely important biological and economic information and systems. Other contributors include an increased dependency on software-based IT applications, and increased use of digitalized industrial control systems for regulated safety processes in the production and storage environments, waste management, etc. These data and information ecosystems are used to verify good manufacturing practices (GMPs), food safety adherence (Hazard Analysis and Critical Control Points [HACCP]), quality standards, and biosecurity practices. All have impacts on upstream and downstream suppliers and vendors.
Moreover, much of the data and information is sensitive and proprietary and essential for remaining productive and competitive, including product development concepts, intellectual property, ingredient supplies, packaging, personal health, and personally identifiable information such as sensory (human subject) personal identifiers. The convergence of biological data with digital technologies and cyber-physical systems and biosecurity considerations relates to every sector in the food supply chain (Duncan et al. 2019).
Patchwork Is Not Sufficient
Relying on IT experts and cybersecurity investments in patching software solutions alone is insufficient to effectively mitigate cybersecurity risk to organizations—and the entirety of the end-to-end food system. Cyber risk is a shared vulnerability, and security is a shared responsibility. Protecting against cyberattacks requires an awareness of the potential consequences of unmitigated cyber risk on food safety, biosecurity, economic competitiveness, and security of supply. Because unmitigated cyber risk can exceed one organization’s reputational losses and extend to losses across a particular industry subsector, or even cause broader reputation losses stemming from general mistrust in the integrity of products from a particular country of origin, cyber risk should be viewed as enterprise risk and requires senior leadership-level attention.
A New Twist: Cyberbiosecurity
Cyberbiosecurity is an emerging discipline at the convergence of cybersecurity, cyber-physical security, and biosecurity (Murch et al. 2018). “Cyberbiosecurity addresses the potential for or actual malicious destruction, misuse, or exploitation of valuable information, processes, and material at the interface of the life sciences and digital worlds,” according to Richardson et al. (2019). Despite its growing importance, this discipline is still a missing component within the food scientist and food engineer training, even though the food scientist/engineer roles are distributed throughout the food supply chain. Food scientists and engineers are aware of the nuances, accepted data variability, and the risks of recalls or product failure if processes, ingredients, or storage conditions are altered or data is lost, locked, or manipulated. As most food scientists are knowledgeable about GMP, HACCP, and other standards, they are inherently responsible for “developing and instituting measures to prevent, mitigate, investigate, and attribute biological, physical, and cyber threats as these pertain to security, competitiveness, and resilience” related to food quality, safety, and security, according to Murch et al. (2018). This gap in education and training increases risks to the domestic food supply chain and the ultimate mission of securing the U.S. and global food supply.
Implications of High- and Low-Effort Cyberattacks
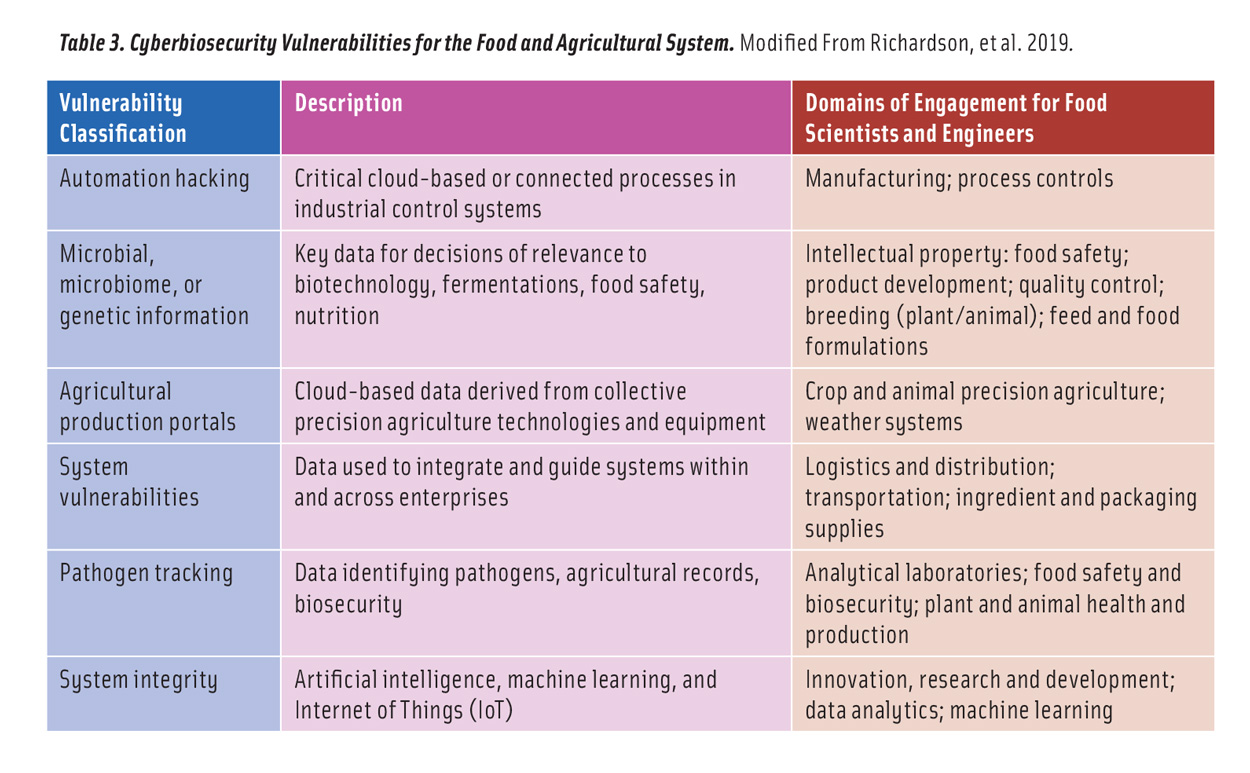
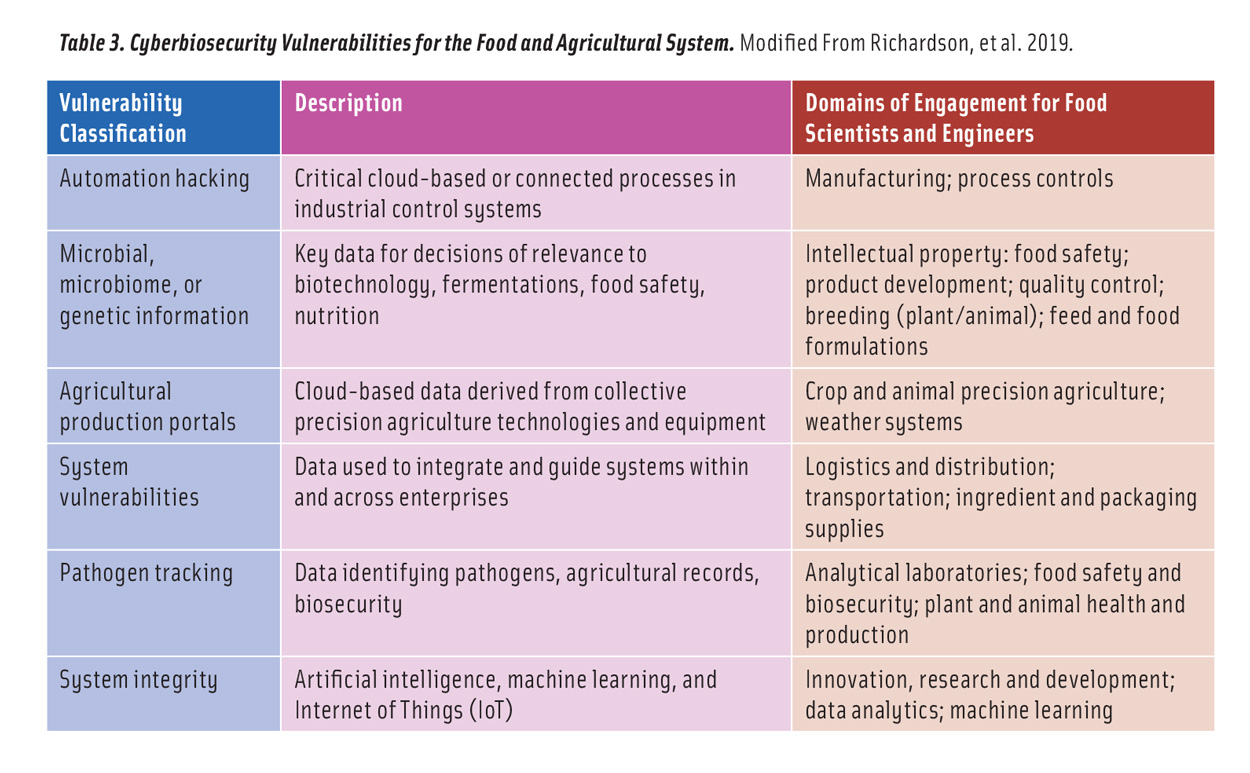
Vulnerabilities exist throughout the farm-to-table system (Duncan et al. 2019, Richardson et al. 2019) (Table 2, Table 3). Cyberbio attackers can engage in high-effort or low-effort attacks. Low-effort attacks are unlikely to result in major losses to major companies or the food system at large but may have larger implications to small- and medium-size enterprises. In contrast, high-effort attacks have the potential to affect critical components of food processing and manufacturing. The result of this effort/return tradeoff is that larger firms may experience many low-effort attacks, most of which can be mitigated with standard IT security tools. More concerning are high-effort and high-payoff attacks that—due to the structure of the modern food manufacturing sector—have the potential for nationwide or even global effects.
The food supply can be fragile and is often managed in a “just-in-time” strategy due to the availability and biology of the raw product. We recently saw this fragility as processing plants were taken off-line as a consequence of labor-related business interruptions during the coronavirus pandemic in 2020, and then as a consequence of various cyberattacks across the food and agriculture sector from development, production, and distribution. These occurrences resulted in significant loss of raw food products and failure to move processed products into markets.
A Susceptible Food and Agriculture System
While advances in technology have increased efficiency in food production, processing, and manufacturing, they have also gone hand in hand with increasing concentration in some food manufacturing sectors. Mergers and acquisitions have resulted in increased company and plant size leading to overall industry consolidation. At the same time, many companies now rely on a high degree of vertical coordination to obtain inputs from producers. The volume of contracted production, and the amount of production managed through vertical integration have both increased in many parts of the food supply chain (Adjemian et al. 2016). These changes in the economic structure of food manufacturing and processing have resulted in a changing cyberbiosecurity risk profile in the industry. Increased connectivity through the IoT has also expanded the potential for susceptibility. Cloud access and storage, rapid advancement of 5G, work from home, and increased use of technology-enabled devices are exposing individuals and businesses to these risks.
Attackers, whether motivated by potential economic returns, or simply wishing to cause havoc, consider both the potential for an attack to be successful and the expected result. While increased concentration may make more resources available for food manufacturers to combat cyberattacks, it also makes single firms into more attractive targets. Generally speaking, the potential payoff from a successful ransomware attack on a major manufacturer is much larger than an attack on a small firm. Likewise, the potential for disruption of food supplies is also much larger. This was seen in recent cyberattacks in the animal processing and slaughter sector, where ransomware attacks on single firms resulted in temporary shutdowns to significant portions of U.S. processing capacity.
Ransomware operators look to target companies that are highly likely to pay ransom demands. Food and agriculture organizations cannot afford downtime, the loss of intellectual property, or the leakage of sensitive information. Given the criticality of producing and processing food, such organizations are high-value targets. In addition, there are nations that are heavily reliant on the United States for food and agriculture.
One way to better defend yourself is to understand the goals of your adversaries. As such, network defenders from the industry often look at adversarial countries’ “five-year plans” to understand what sort of intellectual property they might be looking to exfiltrate.
At the same time, organizations must also defend against insiders. This includes people who act maliciously as well as well-intentioned employees. One way that nations try to gain critical intellectual property is by recruiting employees with technical knowledge away from U.S. companies. In addition, U.S. agriculture and food processing businesses often rely on seasonal guest workers, which makes managing insider threats more challenging.
Securing the supply chain is a systemwide challenge. Many suppliers do not have the resources to sufficiently protect themselves from effective cyberattacks. They can be used as vectors to get into the larger enterprise. Additionally, the use of IoT devices within a sector and the larger system have created additional security concerns. Smart sensors, switches, irrigation systems, and similar technologies all create new challenges and potential attack vectors. Non-malicious insider threats can also lead to bad consequences and often occur due to naivete, ignorance, lack of cyber hygiene, mistakes, or negligence, which reinforces the need for education, regulation, and higher investment in cyberbiosecurity.
What Needs to Be Done?
While there is no single solution to cyberbiosecurity threats, any strategy must comprise a combination of increased education, cooperation, and resource investment.
• Education. As cyber criminals increase their focus on the agriculture, food, and beverage businesses, it is vital to promote education and training on cyberbiosecurity. Last year, Virginia Tech hosted a two-day virtual workshop, “Securing Agriculture, Food, and its Economy (SAFE) with Cyberbio-security,” which included 170 interdisciplinary participants representing state and federal agencies, legislators, professionals from agriculture, cybersecurity, and technology companies and organizations, community leaders, academic researchers, educators, and administrators.
Participants identified the need to customize training for different audiences, explain terms and concepts, and make the topic more approachable. To be effective, communication must be inclusive, and knowledge must be shared through different channels. Large corporations may have the resources to pay for a consulting service or develop their own educational and training materials, but that may not apply to smaller businesses. In this context, land grant universities, through formal and informal education, including their off-campus agricultural research and extension centers and cooperative extension specialists and agents, can play an important role in creating accessible and affordable opportunities to discuss challenges, identify gaps, and share knowledge, good practices, and strategies.
• Information Sharing. Engaging with industry peers to collaborate on cyber risk mitigation has long been considered a necessary and effective practice for critical infrastructure. The threat is simply too great for any company to expect to mitigate on its own. Since 2013, the nonprofit Information Technology-Information Sharing and Analysis Center’s Food and Agriculture Special Interest Group (SIG) has provided food and agriculture companies an industry-only forum to share threat and mitigation information. This SIG assists members to be better prepared through secure and trusted sharing of information and collaborative analysis. Analysts within the SIG have a heavy focus on the strategic side of threat intelligence, often looking toward nation states’ and cybercriminals’ motivations in an attempt to understand future risks and threats. This is often unique to the sector as their global operations require an understanding of foreign policy, tensions, and motivations.
• Resources. Businesses of all sizes should become familiar with the municipal/state/country/trade organizational resources to proactively seek out information and anticipate where to go before and after something happens. In the SAFE with Cyberbiosecurity workshop, the Federal Bureau of Investigation (FBI) advised that defending the food system relied on outreach and education, research and awareness, completion of vulnerability assessments and an advanced playbook, creating countermeasures, having effective detection tools and toolkits, and thorough investigations. Research and cooperative extension publications and websites, workshops, and workforce training programs, and open-source educational materials facilitate learning, planning, and implementation.
Information-sharing communities benefit those organizations with a common commitment to cyberbiosecurity. Information sharing is a force multiplier that enables companies to leverage expertise from analysts in peer companies who are seeing the same threats and dealing with the same business environment. In many ways, the benefits of information-sharing communities extend beyond the sharing of threat information. Leveraging the knowledge and experience of sector peers can empower participants and save an organization time and resources.
And if the worst-case scenario happens and an attack occurs, the FBI also recommended having the local or regional office on speed dial. Invite them into the conversation early.
For a list of resources to learn more about this topic, visit iftexclusives.org/securing-the-food-chain.
Acknowledgements
This work has been supported, in part, by grants and resources from USDA-NIFA Grant No. 2019-67021-29956, Accession No. 1019771, the Virginia Agricultural Experiment Station, the Virginia Tech College of Agriculture and Life Sciences, the Commonwealth Cyber Initiative Southwest Node, and Tyson Foods.
REFERENCES
Adjemian, M. K., B. Wade Brorsen, W. Hahn, et al. 2016. “Thinning Markets in U.S. Agriculture?” U.S. Department of Agriculture, Economic Research Service, EIB-148. doi: 10.22004/ag.econ.232928.
Duncan, S. E., R. Reinhard, R. C. Williams, et al. 2019. “Cyberbiosecurity: A New Perspective on Protecting U.S. Food and Agricultural System.” Front. Bioeng. Biotechnol. 7: 63. doi: 10:3389/fbioe.2019.00063.
Richardson, L. C., N. C. Connell, S. M. Lewis, et al. 2019. “Cyberbiosecurity: A Call for Cooperation in a New Threat Landscape.” Front. Bioeng. Biotechnol. 7: 99. doi: 10.3389/fbioe.2019.00099.
Satariano, A., and N. Perltroth. 2019. “Big Companies Thought Insurance Covered a Cyberattack. They May Be Wrong.” The New York Times, April 15.
Vijayan, J. 2021. “5 Reasons Why the Cost of Ransomware Attacks Are Rising.” https://www.csoonline.com/article/3276584/what-does-a-ransomware-attack-cost-beware-the-hidden-expenses.html.