Defending the Food Supply
Participants in IFT’s 4th Research Summit identified research needs pertaining to potential intentional contamination of the food supply.
How can the safety of the food supply be defended to prevent a terrorist attack? What research must be done to prevent, respond, and recover from an attack? These were among the topics addressed in the Institute of Food Technologists’ fourth Research Summit, held on April 3–5, 2005, in Chicago, Ill.

Research activity on food defense has escalated significantly as a result of Homeland Security Presidential Directive/ HSPD-9, put forward by President George Bush in January 2004. The directive (www.whitehouse.gov/news/releases/2004/02/20040203-2.html) was designed to establish a national policy to defend the United States agriculture and food system against terrorist attacks, major disasters, and other emergencies. It calls for the identification, prevention, and mitigation of critical vulnerabilities in the food supply and for the establishment of university-based centers of excellence in agriculture and food security, such as the National Center for Food Protection and Defense (NCFPD), located at the University of Minnesota.
The Research Summit, cosponsored by NCFPD, brought together state and federal regulatory personnel, law enforcement authorities, U.S. Armed Forces officials, food chemists and toxicologists, public health authorities, and communications experts to discuss and identify research needs in the area of food defense.
Summit Committee Chair Frank Busta, Director of NCFPD, and Program Co-Chairs Douglas Archer, Professor of Food Science and Human Nutrition, University of Florida, and Dane Bernard, Vice President of Food Safety Programs, Keystone Foods, opened the event by presenting the attendees with the challenge to identify research needs that pertain to the intentional contamination of the food supply, i.e., “food terrorism.” They encouraged the participants to focus their efforts to determine gaps and research needed to address the following questions: (1) How do we determine what has happened and what agent is involved in the event of a terrorist attack on the food supply? (2) What is the appropriate course of action to protect public health and food workers? and (3) What is the optimum approach for managing recovery from the event?
Through an iterative, interactive process, the conference participants identified and organized the research needs into five key areas: (1) sampling and detection of contaminants; (2) traceability of food products; (3) decontamination of contaminated products, people, and places; (4) risk communication; and (5) economic impact. This article presents highlights of the presentations. PowerPoint visuals that accompanied the speakers’ presentations are accessible at www.ift.org/cms/?pid=1001028.
--- PAGE BREAK ---
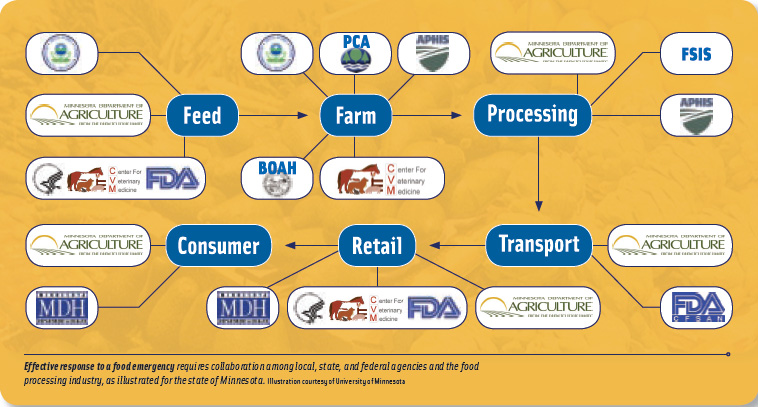 Food Safety and Defense Challenges
Food Safety and Defense Challenges
In his keynote address, Craig Hedberg, Associate Professor, School of Public Health, University of Minnesota, detailed the challenges of defending the new global food system from terrorist attack. Among the challenges, he said, are sourcing of food and ingredients from around the world (e.g., there are more foreign companies registered with the Food and Drug Administration than domestic); increased fresh produce consumption and increasing reliance on foreign sources of produce; and consumption of a significant percentage of meals in restaurants—all of which contribute to a significant number of foodborne illnesses that occur each year.
Hedberg discussed other factors that contribute to the vulnerability of the food supply, including opportunity for access, large batch sizes, uniform mixing, and effective distribution systems. Then he went on to describe the considerable differences between the traditional (forensic) food safety system, which determines why an event happened to prevent recurrence in the future, and food defense, which requires prevention of an intentional event.
He pointed out that the main threats posed by an attack on the food supply include economic disruption, mass anxiety, and mass casualties. He said it is imperative that the food industry harden its defenses to prevent such an attack.
Session discussant Shaun Kennedy, Associate Director, National Center for Food Protection and Defense, University of Minnesota, explained that food defense requires a change in mindset because terrorists do not fear being caught, may be willing to sacrifice their own lives to succeed, and are likely to use unexpected, difficult-to-detect agents.
Detection of Chemical and Biological Agents
Food terrorism is defined by the World Health Organization as an act of deliberate contamination of food for human consumption with chemical, biological, or radionuclear agents for the purpose of causing injury or death to civilian populations and/or disrupting social, economic, or political stability (WHO, 2002). The challenge of sampling and detecting the agent in question in the event of an attack is the subject of much research.
--- PAGE BREAK ---
• Chemical Agents. As evidenced by the list of agents on the Centers for Disease Control and Prevention Web site (www.bt.cdc.gov/agent/agentlistchem.asp), there are many potential attack agents.
Steven Musser, Chief, Instrumentation and Biophysics Branch, Office of Scientific Analysis and Support, Center for Food Safety and Applied Nutrition, Food and Drug Administration (CFSAN, FDA), commented that while the list of hundreds of chemical agents of interest could be narrowed to 12–15, efforts to develop methods for each of these could be insufficient, since there is no guarantee that any of the agents would be used by terrorists. However, research on chemical agent detection is still important because of the heavy dependence of event mitigation, particularly protection of public health, on the detection of the agent and corresponding healthcare needs.
James Coughlin, President, Coughlin and Associates, emphasized the importance of rapid detection methods by calling attention to the differing effect of agent type (unintentional vs intentional) on the typical dose–response curve. A typical curve slopes upward, indicating increasing effect with increasing dose; however, in many cases that slope would be significantly steeper when the agent is selected with the intent to kill. This characteristic presents a considerable challenge to developing detection methods.
Coughlin also discussed physical and chemical characteristics of agents that may allow for their detection and would thereby drive analytical method development. Such characteristics include physical state; chemical class (e.g., inorganic, protein, alkaloid, glycoside); solubility; molecular weight; heat, acid, or light sensitivity; color, odor, or taste; and level of toxicity. These methods themselves should be robust, field-tested, portable, reliable (specificity and sensitivity), quantitative for a specific food product, and universal (food product type and form).
He added that impressive progress is being made in analytical methods development, and referenced work by Tencza and Sipes (2004) that is based on a common property of all chemical and biological agents: the ability to damage mammalian cells. The researchers are working on a method that measures the effects of compounds on cells using a drug discovery technique known as high content screening.
• Biological Agents. Food defense forensics, according to Thomas Cebula, Director, Office of Applied Research and Safety Assessment, CFSAN, FDA, requires going beyond detection at the serotype or serovar level to the strain level, given the need to not only effectively exclude a given strain from association with a source but also attribute a strain to the source involved in a potential biocrime.
He highlighted the utility of oligonucleotide tiling arrays, optical mapping, and real-time pyrosequencing in the identification of biological agents. Tiling arrays provide a high-resolution snapshot of genomes, enabling detection of polymorphisms with >99% accuracy. Optical mapping, which allows identification of insertions, deletions, and rearrangements, can essentially lead to bar coding an entire genome. Pyrosequencing (via luciferase-induced light) enables single nucleotide polymorphism identification and genome organization, and ultimately helps identify and discriminate between related strains.
--- PAGE BREAK ---
Gerry Darsch, Director, U.S. Dept. of Defense Combat Feeding Directorate, U.S. Army Natick Soldier Center, highlighted the food defense–related research pursuits going on at DOD. These include optimized and novel sampling procedures, such as microbial vacuum, through which an entire surface is treated with surfactants and then analyzed; high-surface-area electrospun nanofiber membranes, involving antibody capture; advances in reagents, such as B-cell lines which do not require a secondary antibody; peptide-based capture techniques, using naturally occurring antimicrobial peptides recognizable by cell surfaces; surface-scanning biosensor instrumentation; and a multispectral laser-induced fluorescence imaging system.
Detection techniques being developed, such as those presented by Coughlin, Cebula, and Darsch, may provide the framework for methodology necessary to prevent catastrophic consequences in the event that a terrorist attack on the food supply is successful.
Incident Management
Decontamination after a terrorist event is a critical step in incident management. With respect to biological agents, Bruce Cords, Vice President of Environment, Food Safety and Public Health, Ecolab, Inc., said that peroxyacids, glutaraldehyde, formaldehyde, chlorine dioxide, and ethylene oxide are generally effective against bacterial spores, mycobacteria, and non-enveloped viruses. Phenolics, iodophors, and hypochlorites are generally effective against mycobacterium, non-enveloped viruses, and fungi. Quaternary ammonium compounds and organic acids are generally effective against vegetative bacteria and enveloped viruses.
However, a regulatory hurdle in the use of decontamination substances, he pointed out, is that the Environmental Protection Agency does not allow real or implied claims for activity against any infectious agent that is not stated on the decontaminant’s product label, and very few commercial products have been tested against candidate biological agents of concern.
A true decontamination event does not mimic the tests needed for EPA registration of the chemical, Cords noted, further complicating assessment of efficacy. He also reviewed the preliminary results of studies that Ecolab is conducting for NCFPD in the development of a time–temperature concentration matrix for biocide inactivation of biological agents.
Marcus Cooke, President, Cooke Companies International, reviewed three chemical contamination events and lessons learned from them. The events highlighted were a Baton Rouge chemical fire, Brazilian citrus contaminated by dioxin-tainted lime, and a Belgian PCB-related food crisis. The key phases of such events, he said, are response to the situation, which involves communication and emergency response; containment; and remediation. Experiences surrounding these examples show the importance of using food laboratories and rapid methods (such as immunoassays and cell assays) to identify the contaminant. Additionally, key cleanup steps are product return, centralization, and volume reduction; agent deactivation; release control; and residue disposal.
--- PAGE BREAK ---
Michelle Catlin, Senior Scientist, Office of Food Security and Emergency Preparedness, Food Safety and Inspection Service, U.S. Dept. of Agriculture, reviewed draft “Guidelines for Disposal and Decontamination” that are being developed among various federal government agencies and coordinated by EPA and FSIS. Using decision trees, she showed the various components of and responsible parties involved in discovery and response to a contamination event.
While the affected industry would need to decide how to decontaminate, she illustrated, the decontamination process would need to be developed with and approved by regulatory agencies. Clearance from the Federal Bureau of Investigation would be needed, she said, to begin the decontamination process, and permits for disposal would be needed from EPA or its local or regional equivalent. Catlin noted the limited capacity of local disposal resources and the lack of decontamination techniques for some agents.
Donald Schaffner, Extension Specialist in Food Science, Professor, and Project Director of the Food Risk Analysis Initiative, Rutgers University, reviewed two documents addressing incident management. One originated with the Office of the Deputy Prime Minister of London, and the other was prepared by the University of California’s Lawrence Livermore National Laboratory for the U.S. Dept. of Energy.
The UK document addresses the roles of the various parties—from the building owner/occupier to the fire and rescue service and armed services—who would be involved in an event. The DOE document also describes activities of key parties within the plant, from facility and program associate directors to the environmental protection department and plant engineering. While little information appears to exist on managing the recovery process from a food contamination event, the UK and DOE documents appear to be valuable starting points for creating documents for food manufacturers.
Managing the Communication Process
Since the news media serve as the main source of information on food safety and nutrition for the general public, a first step is to determine the most-effective methods of delivery, including the types of media and appropriate spokespersons, said David Schmidt, Executive Vice President, International Food Information Council.
--- PAGE BREAK ---
He said that an information vacuum exists between expert risk assessments (appearing in scientific, technical, and regulatory documents) and public risk perceptions (appearing via news items, cocktail party conversations, and advocacy group reports). Components of risk perceptions, he mentioned, include catastrophic potential, unfamiliarity, lack of personal control, involuntary exposure, lack of trust in relevant institutions, and media attention.
Food-related issues frequently fall into the “high concern/low trust” category, he said. Among the challenges and barriers to effective risk communication with the general public are that differences exist among individuals in level of desired information; precise information may be too complex to understand; and simple messages may be viewed as incomplete or manipulative.
In his tips for overcoming these types of barriers, Schmidt recommended that communicators know and respect the concerns of their audience, understand and use the ladder of credibility (i.e., who is most credible in the public eye), use clear language, and be acutely aware of nonverbal cues. Furthermore, for effective messaging, he suggested developing three key messages on a given issue, having two to three “proof points” (e.g., third-party validation), repeating the messages, and including relevant or practical actions with the message.
Research Needs Identified
Research needs were identified by the participants through an iterative process. Groups worked on research needs in specific areas and presented their ideas to the larger audience to promote discussion and refinement. The major research needs identified are discussed below.
• Sampling and Detection of Contaminants. Sample preparation can be a laborious and time-consuming process. In the event of intentional contamination of a food or beverage, rapid detection of the agent would be critical to the effective mitigation of the attack.
Marjorie Medina, Research Chemist, Eastern Regional Research Center, Agricultural Research Service, USDA, described the ideal characteristics for sampling methods. She called for common operability (i.e., that everyone samples the same way), ease of standardization among laboratories; and development of methods that are simple, user friendly, inexpensive, universal, adaptable, in-line, and field-portable and that use less sample without a concomitant reduction in sensitivity.
--- PAGE BREAK ---
The following aspects of sampling were discussed by Medina and other participants and identified as research needs: optimization of extraction techniques and streamlining of sample preparation (e.g., by eliminating sample-cleaning and enrichment steps); strategies for coping with low concentrations of agents in large volumes; validated methods; and impact of air and water on sampling efficiency.
While highly sensitive detection methods seem desirable, Musser addressed the issue of false positives and negatives, noting that a test that is too highly sensitive could be disadvantageous if it detects, e.g., toxicants that naturally occur in foods but are not biologically significant. David Acheson, Director, Office of Food Safety, Defense and Outreach, CFSAN, FDA, recommended that as detection technologies are pursued, the extent of product losses emanating from false-positive test results must be considered.
Research is also needed to understand and overcome the methodological limitations associated with food matrices/substrates, according to the group addressing this topic. In-line detection is affected by the viscosity, homogeneity, conductivity, and pH of foods. Better understanding of how the biochemical and physical properties of various food matrices affect agent partitioning and immunological and other detection methods is needed.
Currently, there is no ideal method for even seemingly simple matrices, such as water, said Lawrence Zintek, Chemist, Central Regional Laboratory, EPA. He noted that gas chromatography–mass spectrometry is currently used for analysis but cannot analyze all agents.
• Traceability of Food Products. Should a terrorist event be linked to food, swift identification of the specific food, its source, and its ultimate destination will be critical to mitigate subsequent public health impacts. Darsch reported that DOD has been recognized for development and application of radiofrequency identification (RFID) technology to monitor physical security and track the movement of product.
Research in this area should address product identity, to maintain integrity (tamper-resistance) and prevent substitution (organized theft); technologies that are applicable to the broad range of food products, industry segments, and sizes; “interoperability” of systems in the supply chain; and, finally, incentives for implementation. Research in these areas would enhance food protection and control throughout the food supply chain.
--- PAGE BREAK ---
• Decontamination. To best direct resources toward the development of effective methods for decontaminating people, products, and manufacturing facilities, an understanding of the research that has already been conducted and existing data gaps is needed. Development of multi-dimensional, interrelated data tables that correlate characteristics of various potential agents with those of various food substrates and types of facilities, equipment, and packaging would be useful in elucidating needs for further research into detection methods, decontamination procedures, and validation methodology.
Many participants felt that there is a need for establishment of baseline levels of biological and chemical substances inherent to food production facilities. Such baselines would allow determination, prior to an intentional contamination event, of the extent of decontamination that would be required during cleanup. Test kits for initial screening of facilities must be developed. Such detection methods could also be applicable for verifying the effectiveness of decontamination and subsequent safety of the facility.
In addition to the complexities pertaining to disposal and decontamination of the food plant, Acheson raised a question about how the public should be told to dispose of potentially contaminated product. Information on the proper handling of potentially contaminated food products, including the safe disposal of consumer goods, is needed.
• Risk Communication. Research on risk communication should be conducted to determine appropriate roles and responsibilities, before, during, and after an event, of all stakeholders, including government, food manufacturers, trade organizations, health professionals, other experts, and the media.
Messages for each stage of an event (e.g., during event recovery) must be sensitizing, educating, and reassuring, and must be developed and tailored for target audiences, including workers, consumers, and the government. Knowledge of suitable means for communicating with employees and the public about the safety of a facility and product upon recovery from an event is needed. Information on state-of-the-art technologies and resilient communication vehicles for efficient communication without infringement on proprietary information is also needed.
Participants noted that evaluation of prior tabletop and other training exercises to determine lessons learned, more effective alternatives, preferred training packages, and overall effectiveness for risk communication purposes could be very useful. Additionally, differences, if any, in the risk communication for a real event vs a hoax still need to be elucidated.
--- PAGE BREAK ---
Economic Impact
The economic impact of an act of intentional contamination of the food supply could be massive. Effects range from those that occur within the affected industry, such as jobs and lives lost, to community-based impacts (schools, banks), and broader, ripple-effect impacts. Weak links in the food chain, such as those pertaining to management information systems and industrial organization research, need to be identified. Companies’ willingness to accept cleanup and recovery costs must be determined. However, because nontraditional stakeholders, such as state and local governments which may not be direct consumers, also have an economic impact, better understanding of these sectors is needed. The interests of these stakeholders may prevent the entire cost of cleanup and recovery from being borne by industry. Consumer willingness to pay must also be assessed. Additionally, market structure and the impact of an event (elastic vs inelastic) on a given commodity needs investigation.
The development of tools to compare the costs and benefits of alternative decontamination measures would be beneficial. Research should also be conducted to understand economic incentives to invest in various protection technologies (timing, amount) and identify short-term investments with large future economic impacts. Processes, such as relationship building and infrastructure, that can serve as incentives for information sharing need to be developed. Scenarios and statistical forecasting tools to aid in tabletop and role-playing exercises, along with a collection of case studies that can be used as teaching tools, should also be created.
Database of Chemical and Biological Agents Needed
A major concern of the participants was that a variety of research efforts are currently underway, but that activities and results are not shared. Many felt that a need exists for a compendium or database, comprising ongoing research and results, including the impact of food matrices and effective applications of various technologies; IFT was identified as a logical place for the database.
Participants envisioned the database including information on agents of most likely use by terrorists, and what is known about their interaction with food matrices, methods of detection, and effective decontamination techniques for people, products, facility, waste-water, etc. Mark Wilson, Supervisory Special Agent, Federal Bureau of Investigation Laboratory, noted that when Bacillus anthracis spores were used to intentionally contaminate the mail supply, the particular strain (military Ames) was determined within three days. However, he said, subsequent research was required to obtain information about the strain’s properties and where the strain existed. He suggested that an integrated, multi-agency intelligence database composed of agent characteristics could enable more timely responses to events.
Although this type of information repository would require a major input of time and financial resources, participants felt strongly that its development is critical to accurately identify data gaps and effectively use limited resources.
IFT Plans Food Defense Conference
The Institute of Food Technologists’ 1st Annual Food Protection and Defense Research Conference will be held in Atlanta, Ga., on November 3–4, 2005. The conference will be led by the National Center for Food Protection and Defense in cooperation with the National Center for Zoonotic and Foreign Animal Disease Defense at Texas A&M University, the Food Safety Research and Response Network at North Carolina State University, and the Western Institute for Food Safety and Security at the University of California, Davis.
The objectives of the conference are to report on important discoveries in food protection and defense; create a forum for scientists to exchange information; and enhance research agendas pertaining to food protection and defense.
The most recent research accomplishments to advance the security and safety of the nation’s food supply will be presented. Conference sessions will include Detection and Diagnostics; Modeling and Risk Assessment; Economic Analysis of Events and Response; Education and Outreach; Transportation and the Supply Chain; Food Processing and Decontamination; Risk Communication; and Public Health and Response Coordination.
Further descriptions of these sessions and registration information are available at www.ift.org.
Cory M. Bryant , Ph.D., and Jennifer McEntire, Ph.D., are Research Scientists, Dept. of Science and Technology Projects, Institute of Food Technologists, 1025 Connecticut Ave. N.W., Suite 503, Washington, DC 20036-5422. Rosetta Newsome, Ph.D., is Director, Dept. of Science & Communications, Institute of Food Technologists, 525 W. Van Buren St., Chicago, IL 60607. Send reprint requests to author Newsome ([email protected]) .
References
Tencza, S.B. and Sipe, M.A. 2004. Detection and classification of threat agents via high-concentration assays of mammalian cells. J. Appl. Toxicol. 24: 371-377.
WHO. 2002. Food safety issues. Terrorist threats to food. guidance for establishing and strengthening prevention and response systems. 2002. Food Safety Dept., World Health Org. www.who.int/fsf
