Verifying Supply Chain Data: Why It Matters
Ensuring the veracity of digital information within food industry supply chains has important ramifications related to traceability, sustainability, food safety, and more.
Article Content
In a time of virtualization, especially in the context of COVID-19, the world is seeing how digitization is enabling action from afar in all systems. During this pandemic, the vital human-to-human interactions that keep us together and enjoying food are being digitized. Coinciding with this digitization of human relationships is the digitization of physical assets. For the last decade, technologists have described this transition as Industry 4.0, or the 4th industrial revolution. In Industry 4.0, digital technologies are going beyond human communications to networking and manipulation between machines and the objects they govern (Arsyad et al. 2019). The basic premise of this paradigm is that objects will begin to have their own means of communicating their status and condition, and smart factories, vehicles, and facilities will be able to respond and react to this information (Schroeck et al. 2019). As these novel methods in smart production and manufacturing increase in adoption, the digital information’s veracity and actionability will be paramount.
One chief reason for the food industry to move toward Industry 4.0 methods and thinking is to enhance the ability to systematically trace and track food ingredients and products throughout their life cycles, known as traceability. The use cases for traceability primarily focus on food safety and recall capabilities, but they also can improve supply chain efficiencies, underpin sustainability initiatives, and mitigate other risks, such as human rights violations (Atilgan and McCullen 2011, Gualandris et al. 2015). End-to-end traceability capabilities have increased over the last two decades with the advent of dedicated traceability solution providers, improved methods of asset identification, food traceability data standardization efforts, and market forces for increased accountability and visibility in food supply chains. However, an age-old question in supply chain visibility arises: How can I be certain the data I receive about the product is authentic? Many refer to this quandary as “garbage in, garbage out.” No matter how robust or technologically sophisticated a traceability system is, if upstream supply chain actors lie or provide inaccurate data, the practicality of a food traceability system is undermined.
Ensuring the Data Is True
Before devising a framework for verification, there should be some discussion on what supply chain actors mean when they request data be verifiable. Many may say, “I want to know the data is true.” In a fast-moving supply chain, truth in the data may be relative. Weights may be estimates, or sensors may need recalibration. Does this mean the data is not true? We should first explore why a supply chain actor needs information to be “true.” Primarily, an entity sourcing an ingredient that has data on the origins is looking at the entity responsible (who), the location and time where the entity’s actions occurred (where and when), and what inputs and processes occurred (what and how). Additionally, this information needs to be actionable; the food company needs to be able to make certain claims, perform traceback or mass balance analyses, or reduce liability.
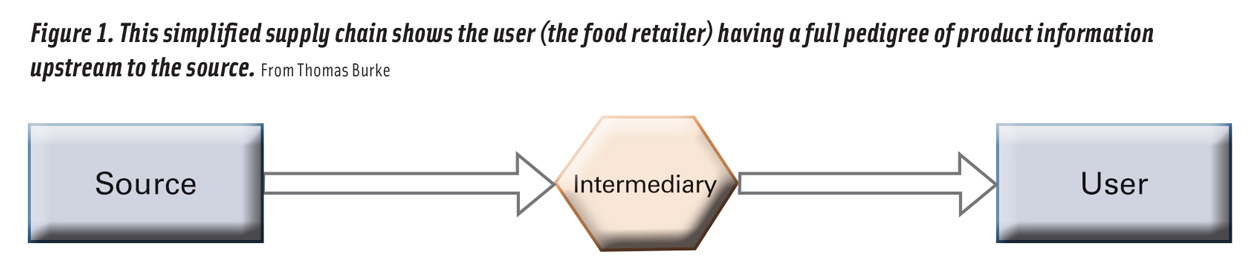
Take a hypothetical scenario wherein a food retailer receives all the desired supply chain information. (Figure 1 shows a simplified scenario.) Associated with the food product’s batch/lot, the retailer can query and obtain data on where each ingredient was sourced, who produced it, and the manner in which it was produced. Despite having this data, the recipient cannot necessarily be confident in it just on its face. The company may desire that the recordkeeping be in accordance with a regulation or a certification scheme to ensure its veracity. The company may also want to be able to check data points with external sources to ascertain validity. In most all fact-checking scenarios, veracity and validity reside in the ability to independently corroborate the data received.
When evaluating supply chains for data accuracy and veracity, the questions on data validity were somewhat less pronounced for food safety scenarios. While this data still has challenges in accuracy, regulatory oversight has driven supply chains to have traceback capabilities in the scenario of a recall. However, as supply chain data reaches further upstream toward production, obtaining accurate and readily available traceability data can be challenging. In sustainability and human rights work on supply chain visibility, there have been two primary modalities to fact-checking: verification and monitoring (Gualandris et al. 2015). In sustainability and human rights, producers and other upstream actors have a great deal of incentive to hide practices that may risk their ability to continue selling their products to their customers. Additionally, these supply chains are often highly globalized, making it more difficult for downstream actors, such as secondary processors or retailers, to be able to effectively monitor and verify data on the ingredients of the foodstuffs they purchase.
In the past, to ascertain the conditions of an ingredient’s origins, a company would do so through monitoring, or the auditing of practices and processes. While not being able to continuously check data validity, an auditing scheme is straightforward to implement and economical to scale. As is familiar to the food industry, third-party audits check against a variety of food safety and sustainability certification standards (Gualandris et al. 2015). These mostly analog methods have many advantages but still are prone to liabilities. On the other hand, verification is a more continuous means of interrogating the veracity of supply chain information accompanying ingredients and products. Rather than checking in periodically to see if best practices are being kept, verification goes toward methods of evaluating accuracy on specific data points or even on an automatic basis (Gualandris et al. 2015). This can be achieved in a variety of ways, depending on how you define verification. Outlined here are common methods and mindsets of authenticating data for digital supply chains in the context of verification: oversight (either by a regulator or other authenticator), data security methods, digital technologies, and corroborating datasets. Overall, it will be illustrated that data verification is not just a technological challenge but a human one as well.
Approaches to Authentication
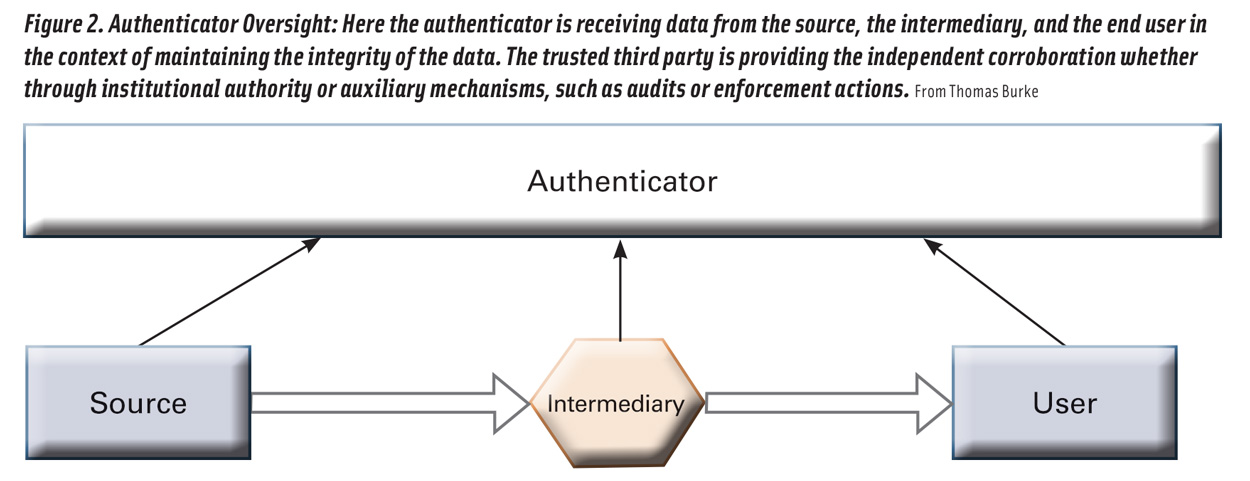
An obvious method of authenticating data validity is having a third party oversee the transmission of data in conjunction with audits and enforcement mechanisms. Though this does not preclude the possibility that data going through the third party were not sufficiently vetted or validated, the position of the third party enables a couple of mechanisms (Manning 2018). First, if the authenticator is a government agency or regulator, the implications of falsifying data are clear: the given entity is potentially violating the statute or regulation. Similarly, a third party that may certify a product for certain claims has the power to rescind that certification if falsified data were input. Merely having this power relationship can enable compliance to a standard to the best of a company’s ability. Second, an authenticator is seeing data across multiple supply chains and should have sophisticated techniques for detecting patterns of irregularity. Given that the authenticator’s mission is focused on collecting and maintaining a standard, whether a certification or a regulation, this will be a priority for them to maintain confidence in their stakeholders. A prominent example in traceability is the Seafood Import Monitoring Program with the National Oceanic and Atmospheric Administration (NOAA) as the third party. NOAA collects traceability data through Customs and Border Patrol as it enters U.S. commerce. Some disadvantages arise in a third-party authenticator scenario. The first is still depending on a good faith actor working in accordance with the standards and best practices laid out under the certification or regulation, and the second is dependent on the given authenticator’s ability to meaningfully evaluate the data. Third, unless an authenticator is overseeing the entire supply chain, there will be gaps where veracity is not attained. (See Figure 2 for an authenticator oversight diagram.)
Data security is intertwined enough with verification that it warrants being addressed here. Though this does not get to the heart of the “garbage in, garbage out” problem, it does at least alleviate concerns about sender authentication and confirmation of receipt by the intended recipient. These may include secure data transmission protocols, such as AS2 (Applicability Statement 2) or HTTPS (Hypertext Transfer Protocol Secure), or familiar methods of user verification, like two-factor authentication. The takeaway to data security as a component of verification is its importance in deterring the occurrence of intruders into a supply chain information network and to reliably ascertain the sender and receiver are the rightful owners of the informational transaction.
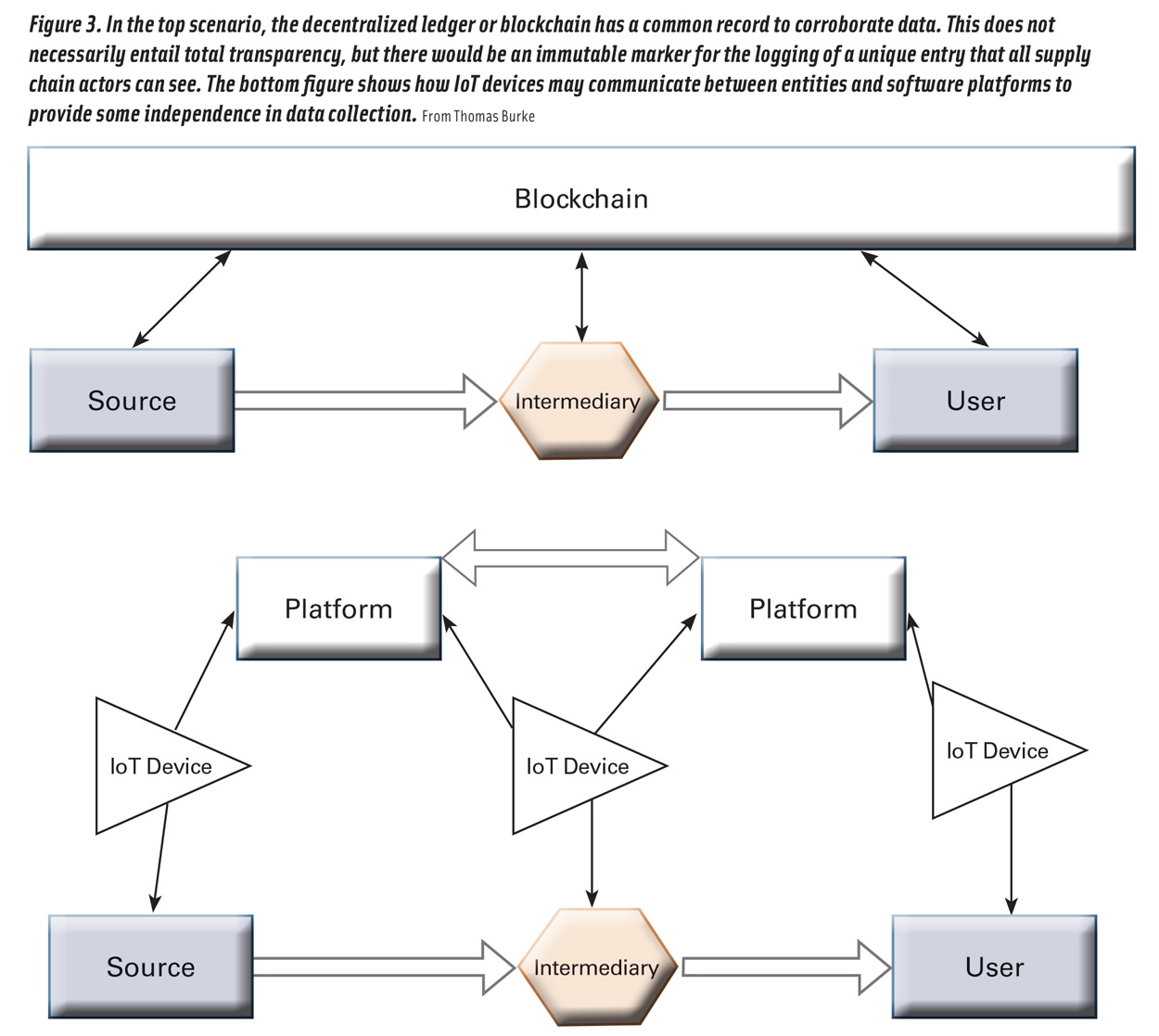
Supply chain digitization technology and tools have driven the most excitement in food traceability but are perhaps the least advanced method. The two technologies that touch most directly on verification and authentication are blockchain and the Industrial Internet of Things (IIoT). A common joke about blockchain is that the technology transforms a lie into a verified lie. While there are elements of truth to this, as it is usually a means of sharing data in a decentralized and immutable architecture, it has been explored as a means of facilitating verification, mainly by having a permanent record to prove that information was logged at a certain time (Arsyad et al. 2019). Devices in IIoT have more possibilities for verifying data streams accompanying products (Witkowski 2017). Because an internet-enabled device or sensor provides a reliable stream of data directly from the object itself, and given that there is sufficient security to that data stream, users of the information garnered from an IIoT device can have relative justification that the data is true. Though this corroboration of data is not exactly independent, IIoT devices move verification challenges from whether the user is truthful toward data security and whether the device’s configuration is accurate. (Figure 3 shows the scenario of using technology to provide the independent corroboration.)
Corroborating Data
Lastly, methods for verification that will likely be key toward future confirmation of food supply chain data are corroborating data. Supply chain data are speaking to physical characteristics of the object’s journey: entities, locations, processes, and conditions. Because of the push for digitized records of locations elsewhere (think Google Maps), datasets from remote sensing sources and other databases can be used to verify data. These confirmatory datasets can be used in conjunction with analytical methods, including machine learning, to give projections of certainty.
Which factors can enable verification? Standardization in object identity, data sharing, and authoritative data sources is key to building tools around food supply chains. Without common expectations for how and where data should be collected, there cannot easily be a market for solutions to work toward. Additionally, authorizing agencies need to be ready to provide comprehensive ability to seek out false information and have appropriate recourse for bad actors. Finally, the ability for machines to directly input data to the system transitions the question from best practices of supply chain actors to data security questions. Of course, there will always be challenges with false identities and “spoofed” data, but these methods only continue to be more technologically sophisticated and less easy to pull off as data collection and sharing become more commonplace.
Data verification has only begun to be explored with the growing expectation for supply chain information beyond an organization’s immediate control. Standardization will continue to be a contributing factor for tools to be created around verification. Correspondingly, costs for the digital technologies enabling supply chain verification will decrease, making the business case for digital supply chains all the more attractive. Overall, the food system will see a transition from a manual periodic evaluation (monitoring) to continuous verification with independent corroborative mechanisms.
REFERENCES
Arsyad, A. A., S. Dadkhah, and M. Koppen. 2019. “Two-Factor Blockchain for Traceability Cacao Supply Chain.” Advances in Intelligent Networking and Collaborative Systems, edited by F. Xhafa, L. Barolli, & M. Gregus. Cham, Switzerland: Springer International Publishing AG.
Atilgan, C., and P. McCullen. 2011. “Improving supply chain performance through auditing: a change management perspective.” Supply Chain Manag. 16(1): 11–19. doi: 10.1108/13598541111103467.
Gualandris, J., R. D. Klassen, S. Vachon, et al. 2015. “Sustainable evaluation and verification in supply chains: Aligning and leveraging accountability to stakeholders.” J. Oper. Manag. 38: 1–13. doi: https://doi.org/10.1016/j.jom.2015.06.002.
Manning, L. 2018. “Triangulation: Effective verification of food safety and quality management systems and associated organisational culture.” Worldw. Hosp. Tour. Themes 10(3): 297–312. doi: 10.1108/whatt-02-2018-0009.
Schroeck, M. K., A. Kwan, J. Kawamura, et al. 2019. “Digital Industrial Transformation: Reinventing to Win in Industry 4.0.” Deloitte Insights. https://www2.deloitte.com/us/en/insights/focus/industry-4-0/digital-industrial-transformation-industrial-internet-of-things.html.
Witkowski, K. 2017. “Internet of Things, Big Data, Industry 4.0 – Innovative Solutions in Logistics and Supply Chains Management.” Procedia Eng. 182: 763-769. doi: https://doi.org/10.1016/j.proeng.2017.03.197.