Protecting the Food Supply
Intentional food contamination resulting from a terrorist attack differs significantly from traditional accidental food contamination. Are food safety measures sufficient for food defense?
The attack on September 11, 2001, motivated the United States government to evaluate the infrastructures that support our way of life to determine which are most vulnerable to a terrorist attack. The food and agriculture sector was one of 17 singled out. This was followed by the passage of legislation (the Bioterrorism Act of 2002) that significantly expanded government authority to prevent, detect, and respond to an attack.
When the target is the food supply, the goal of a terrorist would be to deliver a select biological or chemical agent to the system at a point where it will cause harm and/or economic disruption. There are many such access points within the farm-to-table continuum that make it a highly conducive medium for agent dissemination. These access points, combined with the fact that this is a relatively novel concern for most food companies, theoretically simplify orchestration of a terrorist attack on the food supply.
On December 2, 2004, then Secretary of Health and Human Services Tommy Thompson drew public attention to the vulnerability of the food sector when he said, “I cannot understand why the terrorists have not [targeted] our food supply, because it is so easy to do” (Branigin et al., 2004). Preparedness of food systems to prevent and respond to a potential terrorist attack is guided by documents produced by both the Food and Drug Administration’s Center for Food Safety and Applied Nutrition (FDA/CFSAN) and the U.S. Dept. of Agriculture’s Food Safety and Inspection Service(USDA/FSIS). They include awareness documents and training, defense plans, self-assessment checklists, guidance documents, and inspector training. And significant portions of government funding are going toward expanding laboratory capacity to survey and respond to “exotic” agents.
While these efforts are extremely important and potentially effective for increasing the resistance of the system to an attack, they are heavily focused on physical security measures and personnel screening. There is less emphasis on the nature of a food terrorism event, the interactions between the agent and the food matrix, the effect of food processing on select agents and implementation/adjustment of processing to reduce or eliminate potential agents, detection of the agents, vulnerability analysis training, and the consequences to the food industry.
The objectives of this article are to point out some of the differences between a traditional accidental (or unintentional) foodborne outbreak and an intentional food contamination event, (i.e., food terrorism) and to address the following questions: Do they have the same effect on the food supply? Why is our country’s food supply chain vulnerable to disruption? Do we need to modify existing food safety systems to enhance their ability to prevent, detect, and respond to terrorist acts?
Key Attributes of a Food Terrorism Event
The difference between an accidental (food safety) and an intentional (food defense) contamination event is inherent in the meaning of these terms used to describe them. Accidental food contaminations are typically associated with innate pathogenic microorganisms and their natural proliferation pathways. Intentional contamination, on the other hand, is associated with a select group of unfamiliar agents that typically have high mortality rates. While both have the potential to inflict harm and cause significant economic losses, an accidental incident is not instigated purposely, while an intentional incident is caused by a deliberate action.
A terrorist attack against the food supply chain would target access points that would render the greatest impact—the goal being to cause high morbidity and mortality, widespread economic disruption, and fear. From a motivational perspective, biological and chemical agents offer psychologically powerful tools, with the potential to incite fear, disorder, and potentially panic, although, some believe that the panic would be short-lived (Sandman and Lanard, 2005). Even a minor attack could have a disproportionate impact.
--- PAGE BREAK ---
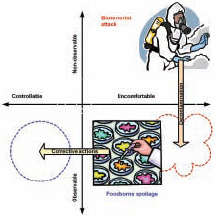 Moreover, a stronger public reaction can be expected when foods for specific population groups (e.g., children and elderly) become targets. The loss of consumer confidence in the safety of the food supply chain is a highly probable result of an intentional contamination incident. On other hand, researchers consistently report that consumers underestimate the risk of illness from foodborne pathogens (Bruhn, 1997). Thus, an intentional food contamination event could be expected to produce a much greater consequence than a traditional foodborne outbreak (Figure 1).
Moreover, a stronger public reaction can be expected when foods for specific population groups (e.g., children and elderly) become targets. The loss of consumer confidence in the safety of the food supply chain is a highly probable result of an intentional contamination incident. On other hand, researchers consistently report that consumers underestimate the risk of illness from foodborne pathogens (Bruhn, 1997). Thus, an intentional food contamination event could be expected to produce a much greater consequence than a traditional foodborne outbreak (Figure 1).
The ideal agent would be highly effective (e.g., potent, stable, colorless, odorless, tasteless) and available (e.g., easily produced in quantities sufficient to achieve the desired consequence, which may vary depending on the objectives of the attack).
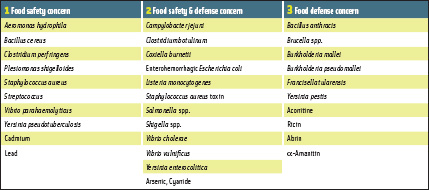 The table on page 36 provides a comparison of biological and chemical agents of concern to food safety (columns 1 and 2; FDA, 1992; CDC, 2005) vs those that pose a risk to national security (columns 2 and 3; CDC, 2005). Some of the agents are “classical” foodborne pathogens (column 2), whose effects the food industry maintains the capacity to mitigate. However, a significant number of high-priority, high-risk agents in column 3 and even some of the more familiar chemical agents in column 2 are not addressed by the traditional food safety systems, increasing food supply vulnerability. These and others could have a significant impact on human health with the potential to overwhelm existing healthcare resources.
The table on page 36 provides a comparison of biological and chemical agents of concern to food safety (columns 1 and 2; FDA, 1992; CDC, 2005) vs those that pose a risk to national security (columns 2 and 3; CDC, 2005). Some of the agents are “classical” foodborne pathogens (column 2), whose effects the food industry maintains the capacity to mitigate. However, a significant number of high-priority, high-risk agents in column 3 and even some of the more familiar chemical agents in column 2 are not addressed by the traditional food safety systems, increasing food supply vulnerability. These and others could have a significant impact on human health with the potential to overwhelm existing healthcare resources.
Foodstuffs constitute highly effective delivery vehicles for select agents for several reasons:
• An intentional contamination could result in undetected, rapid and widespread distribution of agents throughout the supply chain (Fox, 2002).
• Large numbers of individuals may consume the contaminated product.
• Short shelf life and rapid consumption of perishable, ready-to-eat and other food products increase the risk, thereby providing limited time to identify the problem and intervene.
• There may be potential for easy access to the foodstuff at processing or distribution facilities (this varies, depending on the prevention measures in place to reduce access).
• Food processing frequently includes mixing, homogenization, dilution, and/or size-reduction processes, which increase agent proliferation and ensure adequate agent distribution within the contaminated product.
• Pronounced sensory attributes (i.e., taste, flavor, color, texture) of foods effectively mask the presence of contaminating agents.
• The food supply chain has rapid national/regional distribution and just-in-time warehousing, an inventory strategy implemented to improve the return on investment of a business by reducing in-process inventory and its associated costs (Flinchbaugh and Carlino, 2006).
Foods undergo minimal to extensive processing before reaching the consumer. Therefore, the production system and the steps vulnerable to attack are different for each type of food (WHO, 2002). Traditional food processing intervention strategies do not work against all possible agents; in fact, chemical and biological agents exist that are capable of surviving nearly any food process. Additionally, there remains the possibility for entry of the agent into the process at a point in the operation after which no processing takes place, thereby bypassing any step that may result in reduction or elimination of the agent. Furthermore, the lack of systemized data on thermal and chemical resistance of the major agents limits the application of existing food safety measures against these threats.
--- PAGE BREAK ---
Food Supply Chain Vulnerability
The U.S. food supply chain produces about 13% of the nation’s gross domestic product and accounts for 18% of domestic employment. It is one of the most critical components of our infrastructure (Bruemmer, 2003; Khardori and Kanchanapoom, 2005). Organizationally, it is a complex integrated network uniting an immense number of production, transportation, processing, packaging, and distribution facilities that convey food products from the point of growth to the point of consumption.
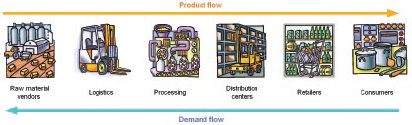 The scheme depicted in Figure 2 shows two major attributes of the supply chain: multi-step transformation of foodstuffs and bidirectional flow of products downstream to the consumer and information upstream to raw materials.
The scheme depicted in Figure 2 shows two major attributes of the supply chain: multi-step transformation of foodstuffs and bidirectional flow of products downstream to the consumer and information upstream to raw materials.
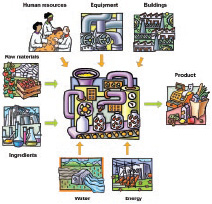 The components that influence the processed food product can be described as food process units, as shown in Figure 3. From a food process unit standpoint, terrorist attacks may occur at many points in the process. For example, such events may include disruption of inbound (e.g., water or ingredient supply) or outbound (e.g., transport) flows of food products and materials. Alternatively, the attacker may directly target food products within the processing facility via equipment and/or personnel (i.e., access points).
The components that influence the processed food product can be described as food process units, as shown in Figure 3. From a food process unit standpoint, terrorist attacks may occur at many points in the process. For example, such events may include disruption of inbound (e.g., water or ingredient supply) or outbound (e.g., transport) flows of food products and materials. Alternatively, the attacker may directly target food products within the processing facility via equipment and/or personnel (i.e., access points).
Some potential failures associated with a food terrorism event are outlined in the following four sections:
• Disruption in Raw Material/Ingredient Flow. Raw materials/ingredients are a highly critical and potentially vulnerable aspect of the supply chain. This is especially important for companies reliant on perishable raw materials and/or just-in-time processing that allows manufacturers to maintain minimal inventories. Disruption due to upstream contamination could lead to a cessation of production, causing major revenue losses. Such disruption is more plausible in a food safety situation because the necessary testing is in place and contamination would more likely be detected, transportation halted, and affected products recalled.
In the event of a terrorist attack, such a testing program (for select or “exotic” agents) would not typically be in place and therefore the contamination would not likely be detected until a later date, if at all. Detection of a food terrorism event would rely heavily on epidemiological data, which means that the contaminated product would be consumed and persons made ill.
Discovery of an agent, receipt of a credible threat, or staging of a hoax could also result in stoppage of inbound and/or outbound transportation services. Such interruption could severely affect the stability of operations and could have an impact on intrastate, interstate, and/or international trade. However, this problem could potentially be alleviated by existing transportation alternatives, except when the use of select agents restrains transport communications in a whole geographic area (quarantine). In that case, the restriction is placed on all inbound shipments, and affected food companies could not arrange alternative shipments for a period of time. This failure is indicative of the increased level of risk associated with an intentional attack vs a traditional contamination. Information on a government/industry initiative to improve border security can be found at www.cbp.gov/xp/cgov/import/commercial_enforcement/ctpat/.
--- PAGE BREAK ---
• Disruption of Processing Facilities. Contamination of equipment and/or facilities may cause company operations to cease for some period of time, especially for small and mid-size companies that lack alternate processing facilities. In the case of an intentional event, there would be potential for an extended lag time before detection of the agent, due to our lack of knowledge with regard to such agents and the unexpected nature of such an event. This additional time would likely preclude the opportunity to recall the affected product unless employees were to become sick before the general public (thus serving as a sentinel or “canary” to alert officials of the attack).
Our lack of knowledge with regard to cleanup and recovery from contamination with exotic agents further differentiates intentional from accidental contaminations. In the post-attack environment, there would be several challenges that a food processor must overcome to mitigate the attack and return the system to normal operation: maintenance of food safety and quality, regardless of probable societal challenges (Branscomb, 2004); disposal of possibly large quantities of contaminated foods—this could prove challenging, particularly if incineration is not an option and decontamination options are nonexistent; and decontamination of affected facilities, irrespective of the particular difficulty that existing sanitizers and decontamination products are not approved for use (at required levels) against select agents and thereby are not (and cannot be) labeled with proper instruction for use in such events.
There is no established procedure for effective and inexpensive decontamination of the food processing facilities from harmful agents. Return to normal operations may be questionable even after decontamination, since most decontaminating compounds are strong oxidizers—their intensive use may result in corrosive damage to the process infrastructure (e.g., equipment, electrical and water supply lines, etc.).
• Systemic Failure Due to Delayed Recognition of the Select Agent. Food production systems are more reactive than preventive, since problems are often discovered after they have occurred (Sobel et al., 2002). The caveat here is that with regard to food safety, the industry has made great strides at preventing accidental contamination, in large part as a result of its active implementation of the Hazard Analysis Critical Control Point (HACCP) approach but that process (as it stands) would not hold up with regard to food defense because the potential agents are unknowns that are not part of the traditional food safety process.
Delayed recognition of an event may lead to inaccurate assessment of the prevalence and incidence of the contaminating agent in the food supply, and thereby has the potential to present a serious threat to public health. Moreover, lack of transparency has made it exceedingly difficult to trace back and identify the source of a contamination (Lachance, 2004; Moe, 1998). This has been improved by the Bioterrorism Act of 2002, which included enactment of stricter recordkeeping regulations. Section 306—Maintenance and Inspection of Records for Foods—requires companies to keep records of the incoming provider and the outgoing receiver of their foods and to make this information available to FDA in the event of a suspected intentional attack (FDA, 2004).
• Disruption in the Product Demand Flow. When an intentional contamination event becomes evident or possibly even suspected—dependent on many influencing factors—a product recall is initiated. Such action will then result in disruption of the outbound flow from the implicated food process/facility and place that facility in uncharted territory with regard to decontamination and disposal. This constitutes a major mode for supply chain failure that requires more insight and consideration.
Consumer Reaction
The consumer’s threshold (or tolerance) for risk increases as familiarity with the proposed danger increases. This threshold is intricately linked with the emotions of fear and trust. Fear is rapidly acquired, slow to diminish, and easy to reestablish; whereas trust is slow to attain, readily eliminated, and difficult to regain (Sandman and Lanard, 2005).
High-risk activities that generate fear are acceptable if they are familiar and voluntary, thereby giving one a feeling of personal control (e.g., bungee jumping). The risks imposed by traditional foodborne contamination can be characterized as familiar but involuntary; however, this is generally acceptable due to the high level of trust generated by our food safety system. To the contrary, intentional contamination would be perceived as unfamiliar and involuntary; therefore, the consumer risk threshold would be very low, and fear would result.
--- PAGE BREAK ---
Traditional food contamination events cause negative public reaction, potentially leading to reduced market demand for the affected food products and/or brands. The post-event effects of foodborne contamination are minimal; the decrease in demand is typically alleviated quickly due to existing corrective actions (e.g., recall) that cause minimal disruption of the food supply chain.
On the other hand, the low level of public tolerance to the risks associated with an intentional contamination would likely cause a significant sustained loss of confidence in the general safety of food. Even after proper decontamination/inactivation of affected areas, fear of food-associated risks may remain, resulting in decreased market demand throughout the food supply chain. Entire groups of food products and brands could be perceived as unsafe. Consumer confidence would need to be restored, and that responsibility falls to the industry and government.
Current thinking supports the theory that even effective mitigation efforts may not prevent the possibility that some products would not return to the market as a result of an intentional contamination incident.
HACCP and Food Defense
HACCP is a safety management system that addresses the analysis and control of biological, chemical, and physical hazards existing in the food supply chain. It is designed to identify health hazards and establish strategies to prevent, eliminate, or reduce (to an acceptable level) their occurrence. Corrective actions are necessary if a deviation from the established critical limits occurs during the processing of foodstuffs.
The HACCP system, in its existing form (www.foodsafety.gov/~fsg/fsghaccp.html) has two major pitfalls that render it ineffective for food defense purposes. First, it was not designed to recognize agents such as those associated with intentional contamination, and food processors have not been highly cognizant of the select agents associated with food terrorism. Second, it lacks standardized corrective actions to resolve post-attack product/facility noncompliance issues.
There is a need to update the existing HACCP system—or in some cases, standard operating procedures (SOPs) and/or good manufacturing practices (GMPs)—with the mechanisms to decrease the potential for intentional contamination of the food supply; appropriate systems to ensure early detection of deliberate food contamination at any point along the production pathway, including surveillance and rapid laboratory diagnostic and communication systems; and systems to ensure rapid and thorough response if an intentional contamination is detected, including protection of employees and consumers.
Additionally, HACCP fails to address all the necessary components for an initial vulnerability assessment. The process for such an assessment endorsed by FDA, FSIS, the Federal Bureau of Investigation, and the U.S. Dept. of Homeland Security is CARVER+Shock (see sidebar).
CARVER+Shock differs significantly from HACCP in that it has been modified from its initial use, which was military based, to consider the less-familiar agents associated with an intentional attack; incorporates vulnerability—an element unique to intentionality and dependent on human ingenuity; and includes many other considerations that are not inherent to HACCP (e.g. accessibility, recognizability and shock).
--- PAGE BREAK ---
The CARVER+Shock process is an important first step toward identifying system vulnerabilities and assigning priority of available resources to hardening the system. Once conducted, the process should be repeated annually or when significant changes in production warrant reassessment. Vulnerable points may be incorporated into an ongoing HACCP program to enable the updates required to modify an existing HACCP program to address food defense concerns.
More information on food defense and vulnerability assessment is available at www.cfsan.fda.gov/~dms/fsterr.html and www.usda.gov/homelandsecurity/sppa.html.
The Challenge Ahead
Deliberate contamination of the food supply chain could have enormous public health and economic impacts. The assessment of a threat to the food supply and the evaluation of the industry’s vulnerabilities form the basis for developing preparedness and response strategies for the food industry. The challenge is to determine the likelihood of various forms of attack and identify the gaps in the existing response systems (WHO, 2002).
Understanding the relationships between the production system, food ingredients, equipment, food workers, and consumers can help identify the vulnerable points where critical failures of the system may occur. The industry can then develop cost-effective measures to enhance its ability to prevent or at least reduce the likelihood of an attack; to detect it at the earliest possible time; to respond in time to protect both the public and the industry; and to recover from an attack by restoring public confidence in, and the economic viability of, affected products.
This brief comparative analysis indicates that intentional food contamination resulting from a terrorist attack differs significantly from traditional food contaminations. Terrorist-induced disruption could quickly propagate throughout the supply chain, creating new avenues for system failure not typically associated with incidents of unintentional contamination. Hence, traditional food safety measures are only partially capable of protecting the food supply. Research is needed to develop sensitive and selective portable detection systems (Graham and Sabelnikov, 2004), to validate on-site rapid detection technologies, study agent/product interaction, and develop proper decontamination and disposal technologies for affected products.
What CARVER+Shock stands for
Criticality (public health and economic impacts)
Accessibility (physical access to the target)
Recuperability (ability of the system to recover)
Vulnerability (ease of accomplishing the attack)
Effect (amount of direct loss suffered)
Recognizability (ease of identifying a target)
SHOCK (psychological effects)
Paul Takhistov, a Member of IFT, is Associate Professor of Food Engineering, Dept. of Food Science, Rutgers University, New Brunswick, NJ 08901-8520 ([email protected]). Cory M. Bryant is Research Scientist, Dept. of Science and Technology Projects, Institute of Food Technologists, 1025 Connecticut Ave., N.W., Suite 503, Washington, DC 20036-5422 ([email protected]). Send reprint requests to author Takhistov.Preparation of this article was supported by U.S. Dept. of Homeland Security Grant No. N-00014-04-1-0659 to the National Center for Food Protection and Defense, University of Minnesota.
www.ift.org
Members Only: Read more about food defense online at www.ift.org. Type the keywords into our search box at the upper left side of our home page.
References
Branigin, W., Allen, M., and Mintz, J. 2004. Tommy Thompson resigns from HHS. Washington Post, Dec. 3.
Branscomb, L. 2004. Protecting civil society from terrorism: The search for a sustainable strategy. Technol. in Soc. 26: 271-285.
Bruemmer, B. 2003. Food biosecurity. J. Am. Dietetic Assn. 103: 687-691.
Bruhn, C. 1997. Consumer concerns: Motivating to action. Emerg. Infect. Dis. 3: 510-515.
CDC. 2005. Agents, disease and other threats. Centers for Disease Control and Prevention. www.bt.cdc.gov/agent/.
FDA. 1992. “Foodborne Pathogenic Microorganisms and Natural Toxins Handbook.” Food and Drug Admin., www.foodsafety.gov/~mow/intro.html.
FDA. 2004. Establishment and maintenance of records under the Public Health Security and Bioterrorism Preparedness and Response Act of 2002. Final rule. Food and Drug Admin., Fed. Reg. 69: 71561-71655. www.cfsan.fda.gov/~lrd/fr04d09a.html.
Flinchbaugh, J. and Carlino, A. 2006. “The Hitchhiker’s Guide to Lean: Lessons from the Road.” Soc. of Manufacturing Engineers, Dearborn, Mich.
Fox, A. 2002. Report of the “Bioterrorism Workshop”: Duke University Thomas Center on April 2-4, 2002, organized by U.S. Army Research Office. J. Microbiol. Methods 51: 247-254.
Graham, T. and Sabelnikov, A. 2004. How much is enough: Real-time detection and identification of biological weapon agents. J. Homeland Secur. Emerg. Mgmt. 1(2): 1-15.
Khardori, N. and Kanchanapoom, T. 2005. Overview of biological terrorism: Potential agents and preparedness. Clin. Microbiol. Newsltr. 27(1): 1-8.
Lachance, P. 2004. Nutraceutical/drug/anti-terrorism safety assurance through traceability. Toxicol. Lett. 150(1): 25-27.
Moe, T. 1998. Perspectives on traceability in food manufacture. Trends Food Sci. Technol. 9: 211-214.
Sandman, P. and Lanard, J. 2005. Adjustment reactions: The teachable moment in crisis communication. www.psandman.com/teachable.htm.
Sobel, J., Khan, A.S., Swerdlow, D.L. 2002. Threat of a biological terrorist attack on the US food supply: The CDC perspective. Lancet. 359: 874-880.
WHO. 2002. Terrorist threats to food: Guidance for establishing and strengthening prevention and response systems. p. 50. World Health Org., Geneva, Switzerland.
